Last Updated on April 14, 2025
Does your information security strategy include alignment with a trusted cyber framework like ISO 27001, CMMC or Zero Trust?
Chris Dorr, practice lead for Pivot Point Security’s Virtual CISO (vCISO) and virtual security team programs, explained the strategic importance of security frameworks on a recent episode of The Virtual CISO Podcast. The show’s host is John Verry, Pivot Point Security CISO and Managing Partner.
Bridging InfoSec strategy and tactics
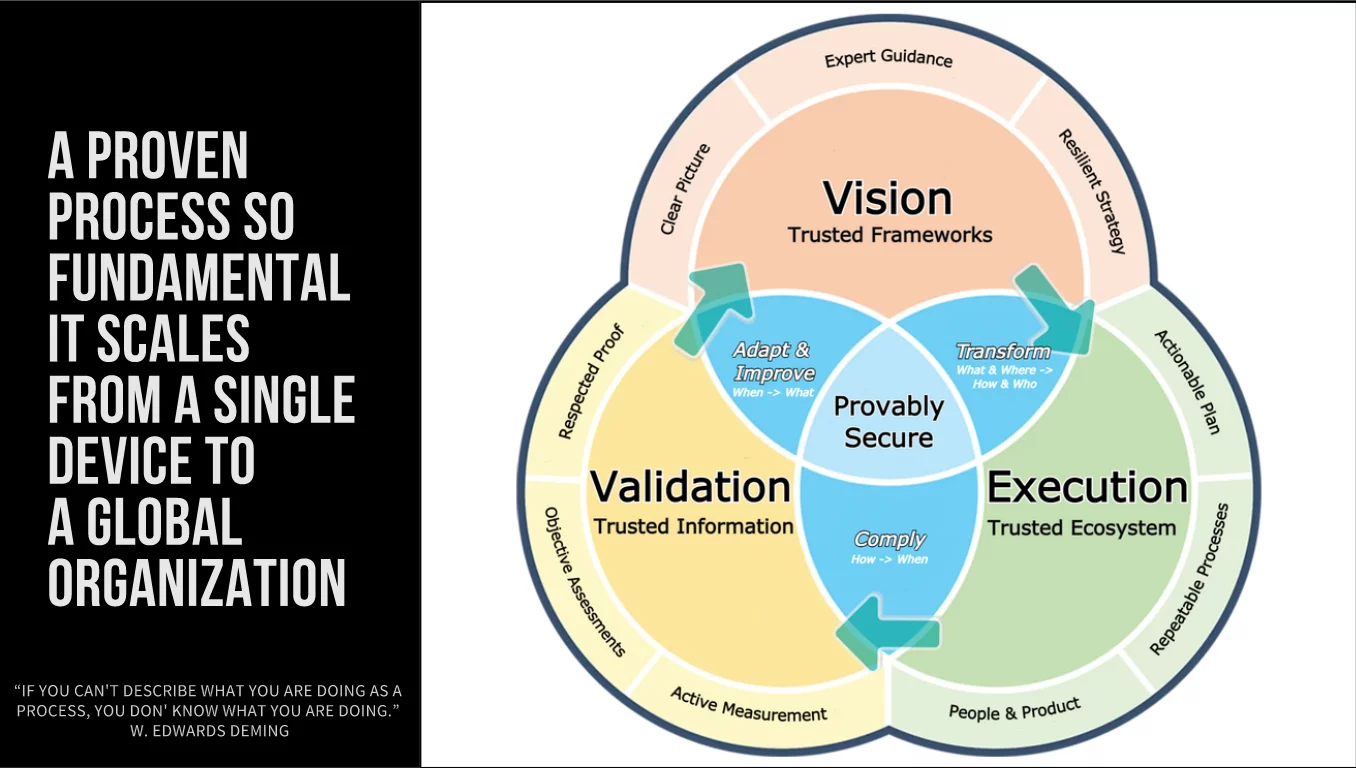
According to Chris, an InfoSec framework is the ideal bridge between strategy and tactics: “A framework connects the two, and not just in terms of very detailed things like controls. [It] provides us a way of establishing a common vocabulary. It establishes a common ground that everybody starts off on. And really it reduces a lot of the friction from building something from scratch.”
“I think the other thing that’s great about frameworks is that frameworks convert the ambiguous to the tangible,” relates John. “When you’re working with an executive and you’re saying, ‘We need an information security management system,’ that is a vague, nebulous term. If I can boil that down to something more tangible, like, ‘I need an InfoSec management committee, they need to meet each month, they need to review an agenda that looks like this…’ I think that framework provides a lot of benefit.”
Supporting staff and process
A trusted framework can also backstop your security team on a tactical level.
As John observes, “We have a problem with not enough qualified, knowledgeable people in our industry. I can hire an information security guy and maybe he’s not 20-years seasoned, which I would like—he’s 5-years seasoned. If I give him a framework, the chance that he’s going to miss something or make a significant mistake goes down considerably.”
But a framework is far more than a checklist.
“It’s not just the individual who’s going to miss something, Chris asserts. “It’s really easy for organizations to miss things. When you’re focused on the details, it’s really easy to miss something critical. Frameworks don’t miss anything critical. For example, ISO 27001 has … 114 controls that are expressly defined. That’s the way that it connects those tactical things to that strategy.”
Aligning product choices
Another tactical challenge that frameworks can help mitigate is interoperability across security products.
“Frameworks make it much more likely that your products will interoperate seamlessly,” says John. As an example, if all your vulnerability assessment tools are talking CVSS, then it doesn’t really matter which scanner I run or whether it’s done in-house or by an external party. It makes sure that that data is interoperable.”
“The other thing [a framework] does is expand the pool of qualified resources,” adds John. “If you’re using the John Verry security standard, your pool of resources is John Verry. If you’re using NIST 800-53 as guidance, your pool of people who are NIST 800-53 knowledgeable numbers in the hundreds of thousands.”
What’s Next?
Ready to transform information security into a competitive differentiator? Don’t miss the strategic expertise that vCISO practice lead Chris Dorr shares in this podcast episode: EP#65 – Chris Dorr – Why Information Security Is Key to Business Strategy – Pivot Point Security
Looking for more guidance to help align your cybersecurity and business strategies? You’ll appreciate these related blog posts:
Here’s How to Fix Your Cybersecurity Program – Pivot Point Security
Step 1 to “Provably Secure and Compliant” – Establish Your Vision – Pivot Point Security