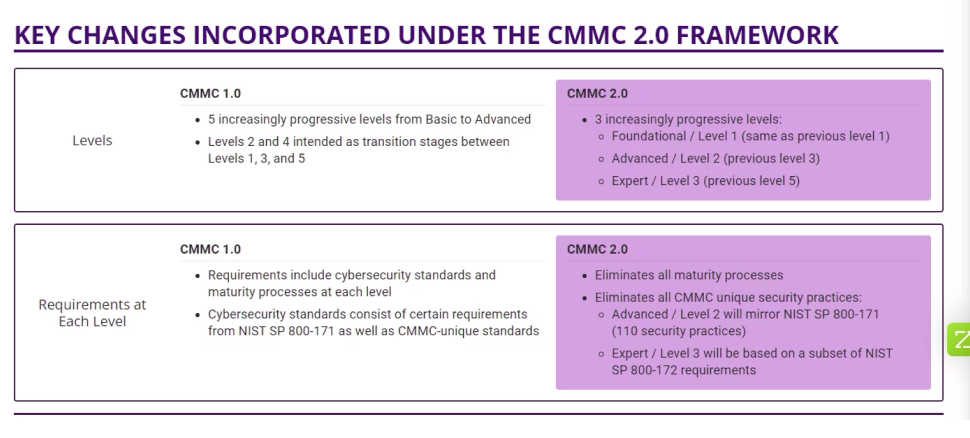
The core of the CMMC—i.e., its Security Domains—currently remains unchanged for CMMC 2.0.
In the most recent version, CMMC v1.02, the framework comprised 17 total Domains, which housed 171 Practices. There were also 43 Capabilities, which functioned as basic measures for the outcomes Practices are meant to ensure.
The breakdown of Domains, Capabilities, and Practices in CMCM v1.02 was as follows:
Domain
|
Capability |
|---|---|
| Access Control (AC) |
|
| Asset Management (AM) |
|
| Audit and Accountability (AU) |
|
| Awareness and Training (AT) |
|
| Configuration Management (CM) |
|
| Identification and Authentication (IA) |
|
| Incident Response (IR) |
|
| Maintenance (MA) |
|
| Media Protection (MP) |
|
| Physical Protection (PE) |
|
| Recovery (RE) |
|
| Risk Management (RM) |
|
| Security Assessment (CA) |
|
| Situational Awareness (SA) |
|
| Systems and Communications Protection (SC) |
|
| System and Information Integrity (SI) |
|
It remains to be seen whether CMMC 2.0 will retain some of all of these Domains, Capabilities, and Practices. It may instead default to NIST requirements.
What are the 43 CMMC 2.0 capabilities?
The National Institute of Standards and Technology (NIST), defines a capability as “a set of mutually reinforcing security controls implemented by technical, physical, and procedural means. The controls that fall within each capability achieve a common information security-related purpose (e.g., Control internal system access).” There are 43 CMMC capabilities, which map to the 17 CMMC domains.
Not all domains specify practices for every capability at every level. For example, some of the capabilities come into play only at higher CMMC maturity levels. However, because the CMMC practices are cumulative across levels, all the lower-level practices will be required at higher levels.
For example, in the Asset Management (AM) domain, there are no practices required for capability C006, Manage asset inventory, until Level 3. This means that CMMC certification at levels 1 and 2 do not mandate compliance with any practices for that C006 capability. Note that the relationship between capabilities and practices, along with the numbering of the practices, have yet to be remapped to the new CMMC 2.0.
What is the purpose of the 43 CMMC capabilities?
Capabilities can be used to simplify the design of a CMMC cybersecurity program as they provide an additional hierarchical mapping mechanism that falls between the 17 Domains and the associated controls. For example, the Access Control domain is mapped to 4 capabilities that logically group the controls within the domain.
Do we have to comply with the CMMC capabilities?
To concretely prove compliance with each capability, an Organization Seeking Certification (OSC) must demonstrate that it adheres to various CMMC 2.0 practices (administrative, technical, policy and process controls from NIST 800-171), including indicators of how well the practices have been operationalized as required for the applicable CMMC maturity level.
How can we leverage the CMMC capabilities to help us get certified?
When you are reviewing/comparing the CMMC 2.0 standard against your environment, the capabilities add additional structure to the [best] practices within each CMMC domain. These “subgroups” can help you judge whether your organization has implemented and culturally adopted a particular set of practices, or not.
For example, if you were to step through the domains and capabilities one by one, you’d probably start with practice AC.1.001 within the “Establish system access requirements” capability within the Access Control (AC) domain. As you go along, you could record the status of each capability (or individual practices) in relation to your chosen CMMC level; for example, as “implemented,” “not implemented,” “not in scope,” etc.
Next Steps
Many DIB companies lack sufficient in-house expertise and resources to prepare for CMMC assessment on their own, especially if they need to comply with CMMC Level 2 (required for handling Controlled Unclassified Information or CUI) or Level 3.
To connect with a CMMC expert to discuss your specific CMMC compliance questions, contact Pivot Point Security.