Last Updated on April 14, 2025
Sometimes TPRM is more art than science.
As a big fan of the TV show “Community” I had to take a peek at the animated show “Rick and Morty” when I learned that Dan Harmon, the creator of Community, was its co-creator. As oddness would have it, the first show I watched involved Rick creating an anti-love potion derived from praying mantis DNA which (unsurprisingly) went quite awry. With a shoulder shrug and a smile, he quipped, “Sometimes science is more art than science.”
What’s odd is that I often complain that the basis of information security, a risk assessment, is also still more art than science. As an engineer, I find that particularly vexing and something that I aspire to address. We recently rolled out some changes to the Vendor Risk Management Programs (VRMP) of a couple of our clients that makes their VRMP “more science than art.”
Identifying High-Risk Vendors
We leverage the type(s) and quantity of data that the vendor may have access to (access, store, process, or transit) as an input into an automated vendor risk assessment (essentially a risk screen) that gives us an understanding of the inherent risk that the vendor poses. In this case, we were reviewing a third-party SAAS provider that was processing financial transactions for our customer’s clients. The Risk Assessment instantly identified 71 “High” risks of note (partial list below) that we needed to ensure were appropriately addressed by the vendors’ information security controls.
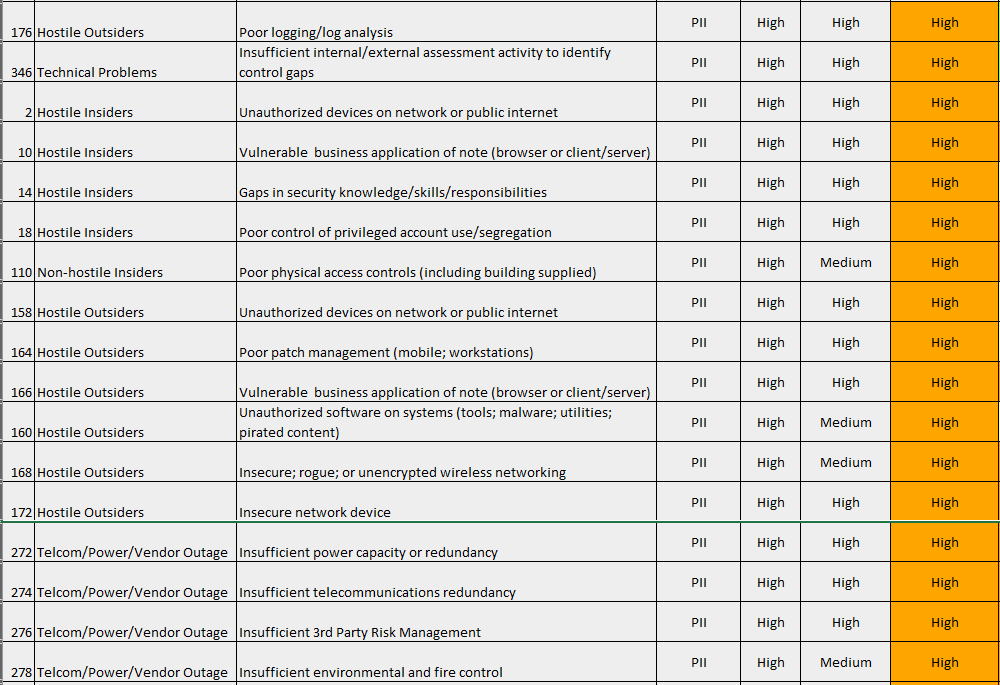
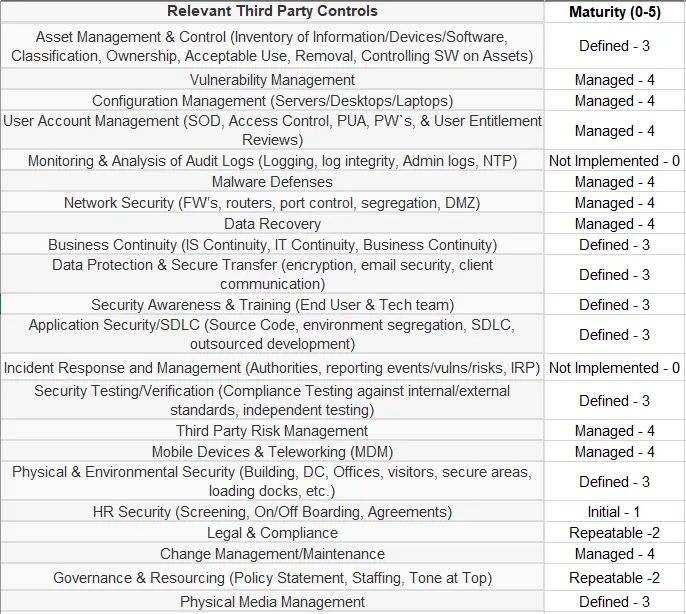
We issued the vendor an Excel-based information security questionnaire to assess the maturity of their security controls. The questionnaire automatically summarizes their information security control maturity across 22 domains.
TPRM Questionnaire
Those controls are then mapped against the specific risks that we identified in the risk screen to automatically generate a measure of the residual risk for each risk originally identified. On review, we can quickly determine that the controls in place do a reasonably good job of mitigating risk.
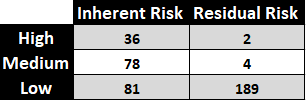
Residual Risk
In this case only 2 of the 36 risks that were originally scored as “High” remained as “High” (highlighted below).
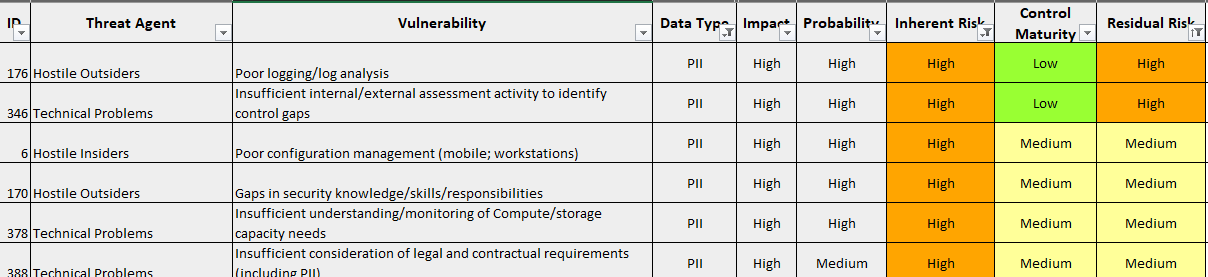
In this case, to close the two “High” risks we required the SaaS provider to implement a logging solution consistent with our client’s requirements and to engage a third party to conduct an application and network penetration test. We also made recommendations intended to address the “Medium” residual risks as well.
What I really liked about the approach we leveraged is that it reduces the level of effort required to conduct the assessment, while at the same time improving the quality and ensuring its repeatability independent of the person doing the work.
You might just say that “Sometimes VRM is more Einstein than Warhol.”


























