Last Updated on February 12, 2025
Here’s an excerpt from a hypothetical meeting between an IT Director and a Business Development Director:
IT: We need to invest in cybersecurity?
BD: Why?
IT: We need immutable backup, we need to enforce multifactor authentication, we need a threat hunting capability, we need new skills within our NetOps and DevSecOps teams, and we need to isolate the many systems that are running an outdated OS.
BD: What is the cost of this “cybersecurity” you speak of?
What’s the problem? Something is getting “lost in translation”—namely a risk-based view that frames the conversation around business disruption, acceptable loss, and identifying and prioritizing risk-based investments to align the organization’s risk posture with its business goals.
A universal translator for IT/business security conversations
Is there a Star Trek era “universal translator” that can turn the IT/business conversation around? Yes. It’s called the NIST Cybersecurity Framework (NCSF). Voluntary, non-regulatory guidance dating back to a 2013 Obama administration executive order, the NCSF was created to help critical infrastructure organizations (or really any business) protect sensitive data with a comprehensive, practical, risk-based approach.
The NCSF is technology agnostic. It is designed to manage cyber risk, provide privacy controls, and improve communication sharing and reporting.
By clearly communicating and documenting business operations requirements using the NCSF, companies can connect technical requirements and existing capabilities or controls to a CSF Profile. This gives business and technical stakeholders a mutually understandable and agreed path forward; that is, an implementation plan. You can think of an implementation plan as a form of gap remediation plan, which lists what is required to get your security program from its current state/profile to its “target” profile/future state or your desired level of cyber hygiene (see Figure 1).
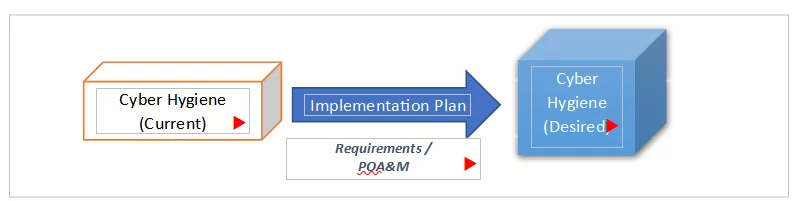
Figure 1: NCSF implementation plan
Implementation Tiers
If your organization has existing regulatory requirements, such as compliance with a DFARS contract clause, the NIST 800-171 standard or the Cybersecurity Maturity Model Certification (CMMC), an NCSF implementation plan will complement or serve as a foundation for those frameworks’ plans of actions and milestones (POA&M) requirements.
Unlike, for example, ISO 27001, the NCSF does not lead to a certification. Also, unlike CMMC, it is not a “maturity model.” However, your implementation plan will directly align with the desired level of rigor for your cyber risk management program, which the NCSF defines using four Implementation Tiers (see Figure 2):
- Partial – at Tier 1, organizations have an informal cybersecurity risk management practice, at best. The implementation of cybersecurity risk management takes place on a case-by-case basis. There is a lack of organizational policies and supporting procedures, which implies a poor ability to enforce and communicate about cybersecurity activities. This includes difficulty understanding the cybersecurity ecosystem, and problems quantifying existing bidirectional cyber supply chain risks.
- Risk Informed – at Tier 2, most organizations prioritize cybersecurity activities based on organizational risk objectives, direct threats to the business, and/or mission requirements. Some levels of the organization communicate about and are aware of cybersecurity risk. Tier 2 organizations are aware of cyber supply chain risk associated with their products and services, but generally take no action to manage, control, and mitigate those risks.
- Repeatable – at Tier 3, organizations have a managed set of cybersecurity risk-informed policies, supporting processes, and procedures. Cybersecurity risk is monitored. Senior leaders, IT and non-IT, communicate cyber risk at various levels of the organization. The organization is aware of its cyber ecosystem and the potential cyber supply chain risks, and often manages those risks.
- Adaptive – at Tier 4, in addition to having well-established risk-informed cybersecurity policies, processes, and procedures, the organization works towards continuous improvements and quickly adapts to the changing threat landscape. Cybersecurity risk and organizational objectives have a direct relationship to business decision-making, and budgeting occurs based on risk tolerance. The organization is well aware of how its stakeholders could be affected by the cyber supply chain risk ecosystem and proactively communicates risk, building a strong supply chain.
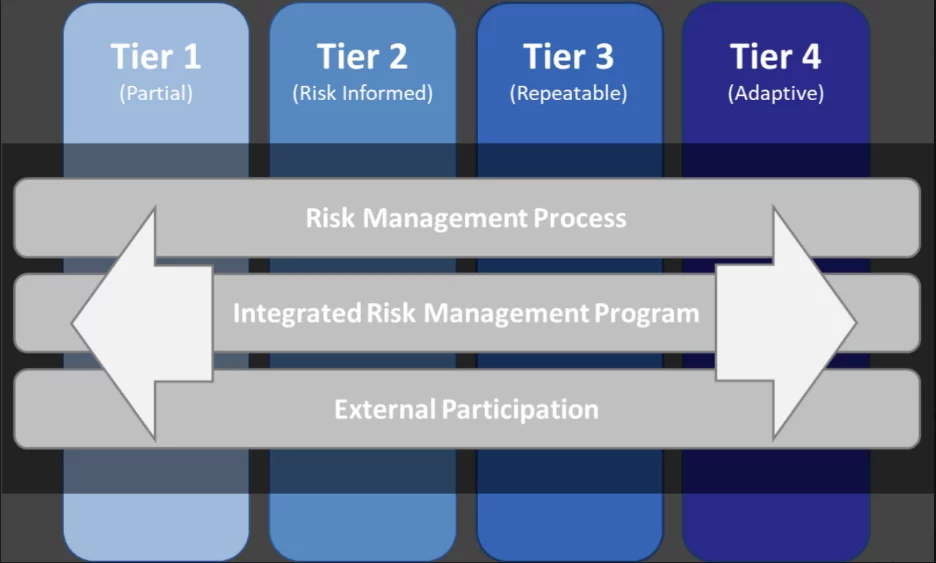
Figure 2: NCSF Implementation Tiers
Mapping improves flexibility and alignment with your goals
NCSF mapping makes its implementation as dynamic or as specific as your organization needs it to be. Many organizations find it relatively simple to align the NCSF guidance to other standards, including ISO 27001 and CMMC, in addition to NIST 800-53 and even the newer NIST 800-207, on zero trust architecture. Figure 3 overviews the flow of a typical NCSF implementation process.
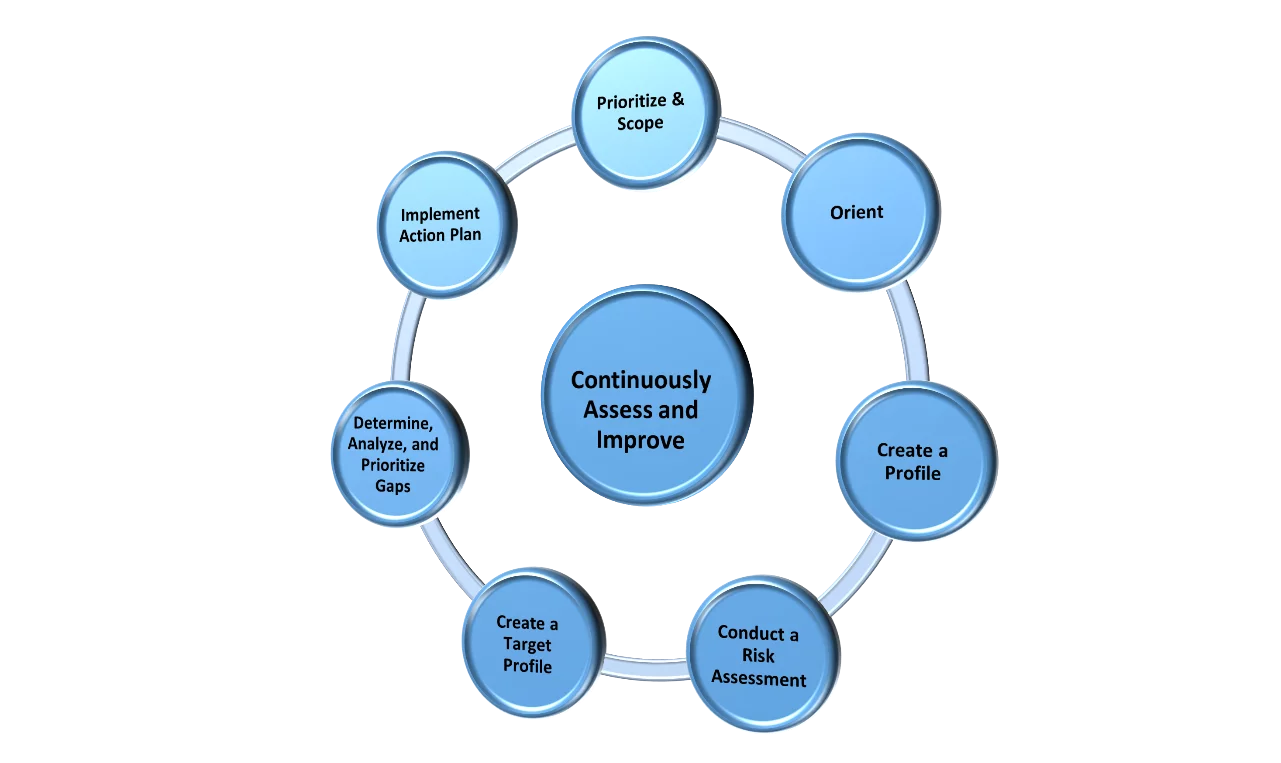
Figure 3: NCSF implementation process
NCSF’s “five functions”
NCSF is famous for its “five functions,” the framework’s high-level organizing principle. The five functions represent the five key elements (aka “pillars”) of a holistic and successful cybersecurity program. Applicable to firms of any size, including SMBs, the five functions also simplify the process of talking about cybersecurity risk management at a high level and supporting risk management decisions in line with business goals.
The five functions are:
1. Identify – ID: The Identify function is all about identifying what you need to protect: physical and software assets, your overall business environment, any existing policies, vulnerabilities and threats you face, and more. If you’re a fan of our podcast, The Virtual CISO Podcast, you may have heard references to the Federal Information System Standard (FIPS) 199, which is the standard that establishes security categories for federal information systems. This standard helps with the classification and categorization of your data; and, based on its sensitivity, helps you determine what controls you need to protect the confidentiality, integrity and availability of the assets affected by the data. This is where you plug in your organization’s data categorization (e.g., IP, FCI, CUI, PII/GDP, EAR/ITAR, PCI, HIPAA, etc., etc.).
2. Protect – PR: Based on a self-assessment of your organization’s operating environment and data sensitivity, you then select the controls or safeguards necessary to protect your assets. This could also involve selecting what control framework to align with, e.g., NIST 800-53, NIST 800-171 or ISO 27001.
3. Detect – DE – Defines what controls you need to identify the occurrence of a cybersecurity event in a timely manner. This could include continuous monitoring (ConMon), Audit Records Reviews, proven and tested detection capabilities, etc.
4. Respond – RS: Includes functions that help you take action when you detect a cybersecurity incident/event, so you can contain its impact. This includes not just the ability to respond to indicators of compromise (IOCs) but also to analyze, mitigate, report and improve your program.
5. Recover – RC: Identifies controls to help you recover after an incident, restore your business processes, communicate with stakeholders about the incident, and improve your program.
Putting it all together
The strength of the NCSF is its simplicity, and its ability to help senior leadership understand cybersecurity programs in a risk-based, business-centric context. This gives companies a starting point for aligning security with business strategy.
But there are still a lot of tactical decisions to make along the way. What controls to implement? How to prioritize technology investments? Where to get skills and expertise?
This is where a trusted advisor like Pivot Point Security, with its Proven Process, compliance expertise and virtual CISO/Virtual Security Team services can help you address operational and organizational risk while also achieving the “provable security and compliance” that your stakeholders are likely demanding.
To talk about your security and privacy goals and how we can help, contact Pivot Point Security.
CBIZ Pivot Point Security has helped hundreds of organizations of all sizes understand their cybersecurity posture utilizing the NIST Cybersecurity Framework (CSF). We utilize risk assessments, gap analysis, maturity modeling and more to help organizations understand their current and target cybersecurity goals.



























