Network Information Security
Safeguard Your Systems Against Cyber Threats and Vulnerabilities
CBIZ Pivot Point Security, a leader in network security solutions, specializes in protecting your data, systems, and networks from advanced cyber threats. Our team of experienced professionals will work together with your organization to conduct the necessary assessments (e.g., vulnerability assessments, penetration testing, cloud security posture assessments) necessary to meet your security and attestation requirements. With our tailor-made security assessments and CREST-accredited expertise, we ensure your infrastructure remains provably secure and compliant.
Where Does Network Security Begin?
Network security refers to the policies, processes and controls in place to protect network infrastructure from unauthorized access or misuse. Organizations often need to prove their network is secure and must accomplish this with limited resources. By assessing your network security, we can provide you with a comprehensive remediation strategy and an understanding of your overall risk. Clients who work with us can prove to key stakeholders their network is secure and know how to prioritize valuable resources.
Testing network security and infrastructure comes in a few flavors depending on your current security posture and where you would like to be. Based on those factors, we can recommend the best course of action for you to reach your desired level of security and prove it to key stakeholders.
Common Network Security Assessment Methods
Ready for a Network Security PEN Test?
Key Challenges in Network Security
Some of the main challenges in network security include:
- Resource constraints and prioritization.
- Cost management and budget allocation.
- Staying ahead of emerging cyber threats.
- Balancing security with user experience.
- Complexity of managing diverse technology.
- Regulatory and compliance pressures.
- Proving security posture to key stakeholders.
Choose CBIZ Pivot Point Security for Network Security Solutions
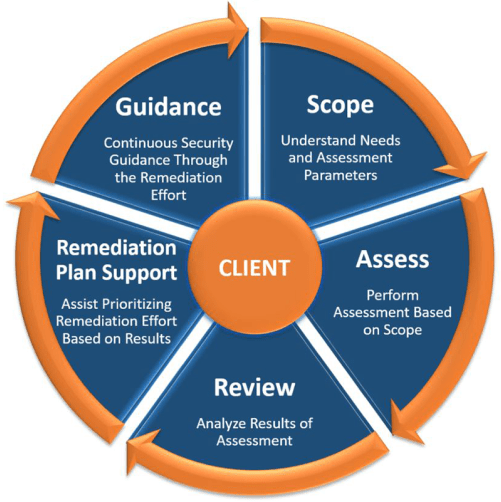
We follow our proven network security consulting process, which involves:
- Assess: Identifying network vulnerabilities and potential threats through a thorough evaluation aligned with stakeholder assurance needs
- Scope: Understanding network-specific risks, compliance requirements and regulatory obligations to establish a solid foundation
- Review: Analyzing security gaps in detail, prioritizing them based on potential business impact and compliance considerations
- Guidance: Providing expert recommendations and strategic roadmaps to ensure alignment with industry best practices and security frameworks
- Remediation plan support: Assisting in implementing, tracking and validating fixes, ensuring all gaps are addressed effectively and in compliance with standards
Our Approach
We base our approach on what our clients care about:
- Rotating pen testers each year: We never have the same tester approach your system two years in a row. There is no need to search for a new pen tester every year which will save you time.
- Getting security metrics: Since we are testing your system on a consistent basis, we have benchmarks for where we began, what was fixed and what still needs to be addressed. Expect actionable security metrics for IT Managers to gauge progress, manage priorities and continuously improve.
Our Staff
Every consultant you speak to is a full-time employee. We believe staffing our organization with quality full-time experts gives our clients a level of service a one-and-done contractor cannot provide. They have deep expertise across various industries and a commitment to long-term client partnerships.
Our Process
Your business is unique and brings its own unique challenges. We understand this concept, which is why we tailor our methodologies to different business needs. Our solutions are industry-compliant across diverse organizational structures.
Our Network Security Solutions
We provide these security services in network security:
CREST Network Penetration Testing
Compliance-driven testing aligned with regulatory requirements helps identify and mitigate potential security vulnerabilities. It helps secure your users, infrastructure, applications and data.
Network Vulnerability Assessment
The aim of the assessment is to:
- Detect configuration errors and missing patches through automated scans.
- Provide insights to strengthen security defenses.
- Help ensure compliance with regulatory requirements such as HIPAA and PCI-DSS.
- Identify gaps in security controls and provide actionable remediation steps.
- Support continuous monitoring and improvement to maintain a secure environment.
Network Penetration Testing
Network penetration testing involves simulated attacks to identify and exploit vulnerabilities. It combines automated and manual testing for comprehensive results.
Network Architecture Review
A network architecture review involves an in-depth analysis of network configurations and security controls. The aim is to ensure alignment with business and compliance objectives.
Why Trust Us?
CBIZ Pivot Point Security is your partner in fortifying your network’s defenses. Our track record of successful projects, combined with our commitment to excellence, allows us to confidently guarantee the effectiveness of our solutions. We’ll only bill you if we accomplish your goals. From achieving compliance to mitigating risks, our proven strategies protect and enhance your security posture.
We use a risk-centric tiering strategy to categorize your network vulnerabilities based on their criticality to your business. You will have a clear understanding of where to begin and a roadmap to arrive at your preferred destination.
We know every business is different, so we tailor our approach to fit your specific needs. From checking your current security to setting up ongoing protection and handling any problems, we’ll be there for you. We’ll help you follow best practices, meet regulations and build a strong defense against cyberattacks. With us, your business will be provably secure.
Network Security FAQs
Network security solutions include both hardware and software, as well as rules and configurations to govern network usage and access. Some examples of network security solutions are:
- Firewalls
- Intrusion protection systems (IPS)
- Virtual private network (VPN) gateways
- Network analytics
- Endpoint detection and response (EDR)
- Network access controls
- Antivirus/malware protection
- Mobile/wireless security
- Web application firewalls (WAFs)
Network security assessments typically involve vulnerability assessments, penetration testing and architecture reviews to identify security gaps and provide remediation plans.
Network security certifications are credentials that validate a security practitioner’s knowledge of best practices. The most popular ones include Certified Information Systems Security Professional (CISSP), Certified Information Systems Auditor (CISA), Certified Ethical Hacker (CEH) and Council of Registered Security Testers (CREST) accreditation for penetration testing providers.
A vulnerability assessment (VA) is an automated way to gather data about issues on your network, such as missing patches or bad configurations. A penetration test almost always includes a VA to inform the testing. It uses the VA and other data obtained via reconnaissance to attempt to exploit any vulnerabilities identified and gain some level of unintended access to systems or data.
So, while a VA will inform you on “how vulnerable you are,” a penetration test will inform you as to whether those vulnerabilities can be exploited and, if so, what the impact could be on your organization.
A vulnerability assessment (VA) is an automated way to gather data about issues on your network, such as missing patches or bad configurations. A penetration test almost always includes a VA to inform the testing. It uses the VA and other data obtained via reconnaissance to attempt to exploit any vulnerabilities identified and gain some level of unintended access to systems or data.
So, while a VA will inform you on “how vulnerable you are,” a penetration test will inform you as to whether those vulnerabilities can be exploited and, if so, what the impact could be on your organization.
You really can’t, just as you can’t really tell if a colonoscopy was a good one. The best way to ensure you have a “good” penetration test is to verify that the vendor has an independent attestation regarding the quality of their methodology and the individuals doing the testing (e.g., CREST certification).
The scope of a penetration test should be determined using a risk-based approach. Consider the following key factors to frame the penetration test scope:
- Asset protection: Identify the assets you need to protect, including sensitive data and critical systems.
- Threat landscape: Determine potential threat actors and their capabilities.
- Infrastructure details: Include cloud environments, DMZ, external/public systems and internal network segments.
- Regulatory compliance: Assess applicable laws and regulations such as PCI-DSS and HIPAA.
- Concurrent testing activities: Account for any other ongoing assessments such as performance or UAT testing.
- Security measures: Consider multi-factor authentication requirements and active defense mechanisms.
- Business impact: Evaluate the potential consequences of a successful attack on the organization’s critical business operations. This could include financial losses, reputational damage or loss of customer trust.
- Data sensitivity: Beyond identifying sensitive data, assess how data is handled, transmitted and stored across different systems, ensuring the scope includes testing for vulnerabilities in data protection mechanisms.
- Access control mechanisms: Examine the effectiveness of role-based access controls (RBAC) and least privilege principles across systems. This includes testing user permissions and ensuring users can’t access data or systems beyond their legitimate needs.
- Third-party services and dependencies: Consider external vendors, contractors or service providers that have access to critical systems or data. The scope should account for risks associated with third-party integrations and APIs.
By addressing these factors, organizations can ensure a comprehensive and effective penetration testing scope.
Get Started With Your Network Security Today
Protect your organization from cyber threats with our expert security solutions. We stand by our services with a 100% satisfaction guarantee and are ISO 27001 certified to ensure your data security meets the highest standards. Contact us today to schedule a consultation and safeguard your critical assets.