ISO 27001
Achieve & Maintain ISO 27001 Certification
Pivot Point Security provides services to help clients achieve and maintain ISO/IEC 27001 certification, the international “gold standard” for information security. Our team will guide you through the ISO 27001 certification process, including defining your information security management system (ISMS) scope and objectives, identifying potential risks to your data, and developing control measures to reduce those risks. We will also help with policies, procedures, and documentation, which are a critical part of ISO 27001 certification. With Pivot Point Security’s ISO/IEC 27001 expertise, you can rest assured that your organization will achieve its certification and security goals.
What is ISO 27001?
ISO 27001 is the world’s most trusted cybersecurity framework. It specifies a set of best practices for an Information security Management System (ISMS). An organization can use these policies, procedures, and technical controls to effectively assess and manage information-related risk.
A key reason to align your information security program with ISO 27001 is that you can be certified compliant by an independent third party. An ISO 27001 certificate is the global “gold standard” to prove you can protect sensitive data.
The ISO 27001 framework is robust and comprehensive, but also flexible to meet diverse business needs. It guides you to “your destination” (provable security and compliance) but lets you choose “the best route” (your Actionable Plan). ISO 27001 also drives continuous improvement as part of its three-year recertification cycle.
Pivot Point Security is a leading consulting firm for ISO 27001 certification and has a 100% success rate bringing over 100 organizations of all sizes to certification.
Want more information on ISO 27001? Check out this episode of The Virtual CISO Podcast.
ISO 27001 certification requires that management:
- Systematically examines the organization’s information security risks, taking account of the threats, vulnerabilities and impacts;
- Designs and implements a coherent and comprehensive suite of information security controls (defined by ISO 27002 (formerly 17799)) and/or other forms of risk treatment to address unacceptable risks; and,
- Adopts an overarching management process to ensure that the information security controls meet the organization’s information security needs on an ongoing basis.
Another benefit to ISO 27001 compliance is that an organization adhering to the 27001 standard can also simultaneously fulfill other compliance requirements including HIPAA, PCI, Sarbanes Oxley, and Identity Theft/Personally Identifiable Information regulations with minimal additional effort.
If you require more information please call 888-PivotPoint and ask to speak with one of our Practice Area Managers or send us an email.
Benefits of ISO 27001 Certification
- Offers definitive proof to key stakeholders that you can protect sensitive data and are in compliance with legal and regulatory requirements (e.g., HIPAA, PCS/DSS, SOX)
- Gives your organization market advantage by differentiating you from competitors
- Significantly enhances your information security posture and greatly reduces the likelihood of a data breach as well as its potential impacts and costs
- Improves overall business resilience and reduces business continuity risks
- Helps ensure your information security program supports business goals
- Increases organizational efficiency and effectiveness
- Lets you focus on growing your business instead of worrying about how vulnerable you are to cyber attack
- Generates substantial ROI
- Leverage other ISO 27000 family certifications, such as our ISO 22301, to add even more value
ROI from ISO 27001 certification
While it can be difficult to quantify, ISO 27001 certification delivers a positive and sustained ROI for almost any business.
An ISO 27001 certified Information Security Management System generates ROI in two major ways:
- Value preservation through reducing business risk, such as decreased probability of a data breach and associated cascading cost and reputational impacts
- Value creation through sales enablement, such as retaining current customers and winning new customers.
Depending on your market and business size, these factors could have a major positive impact on your bottom line. Just dodging one ransomware attack could save you around $250,000 to $850,000—enough to pay for your ISO 27001 certification and then some. An ISO 27001 ISMS also delivers more tangible savings, like increased return on your overall cybersecurity investments.
On the plus side, being able to prove you’re secure and compliant is a competitive differentiator and positions your business as trustworthy and mature. Trust is a lubricant that helps close more deals. Likewise, the ability to meet strict security requirements can help you win bigger contracts with bigger clients.
ISO 27001 Certification Process
In today’s world, you can’t just claim your business can manage data securely—clients, management, regulators, and other stakeholders want proof.
With Pivot Point Security as your trusted partner, achieving ISO 27001 certification and maintaining it year over year is a guaranteed reality. Over the last 16 years, we’ve helped dozens of firms get and stay ISO 27001 certified. Our success rate bringing clients to ISO 27001 certification is 100%.
It all starts with our Proven Process to achieve ISO 27001 certification. Phase 1 clarifies where you are, where you want to be, and how to get you there. Phase 2 executes your plan, operationalizes your ISO 27001 program, validates its effectiveness, and delivers your ISO 27001 certification.
Your initial ISO 27001 certificate is good for three years, after which you’ll need to undergo another certification audit. Annually during each three-year cycle you’ll undergo what’s called a surveillance audit, which is less intensive than a certification audit and more about validating processes than scrutinizing documentation.
This ongoing cycle of certification is why you shouldn’t implement ISO 27001 just to get the certificate. And why it’s beneficial to have a trusted partner like Pivot Point Security to help keep your information security program moving forward.
Maintaining ISO 27001 certification
Obtaining an ISO 27001 certificate is an accomplishment any company can be proud of. But, like everything in cybersecurity, it’s not “one and done.” Sustaining “continuous compliance” with ISO 27001 year over year to keep your certification is a significant challenge.
Many of our clients prefer having our ISO 27001 experts manage their ongoing compliance efforts. This approach gives you:
Peace of mind
Whether it’s scheduling mandatory meetings, reviewing continuous improvement objectives, or informing executive leadership, our clients rest easy knowing an ISO 27001 expert is driving the key components to keep them certified.
Time back to do your real job
Maintaining ISO 27001 certification is time-consuming. Clients who entrust us with their certification maintenance get all that time back… feel free to use it however you want!
Keep your organization on track
Maintaining ISO 27001 certification isn’t rocket science, but there are lots of little things that need to get done—and get done on time. We often see organizations with the best intentions of maintaining certification drift off-course. That doesn’t happen to our clients.
To learn more about how we can help you maintain your ISO 27001 certification, reach out!
Automation to support your ISO 27001 program
ISO 27001 is all about your Information Security Management System (ISMS)—it impacts your whole business, not just a few IT folks. To help our clients operationalize their ISO 27001 practices and processes and get maximum value from those investments, Pivot Point Security has developed three tools:
OSCAR GRC platform
OSCAR addresses the three biggest challenges companies face with achieving and maintaining ISO 27001 certification:
- Moving from “getting certified” to making ISO 27001 best practices part of how you do business every day
- Ensuring that the “trusted information” about your ISO 27001 program needed by your senior business and technical leaders, IT staff, internal/external auditors, etc. is complete, accurate, and available on-demand
- Executing and evolving an information security program at a fast-growing company that needs to stay in compliance with two or more security/regulatory frameworks (e.g., ISO 27001 and CMMC)
OSCAR is that “single source of truth” that tells you whether your ISO 27001 program is on track, what you need to do next, and whether any tasks are overdue. It even assigns tasks to the right people and sends them reminders—so everyone knows what needs to be done when to make sure you remain provably secure and compliant.
OSCAR can even import security data from other sources, like Qualys or Nessus. It can also support your Vendor Risk Management (VRM) program (or help you start one).
To get more details on OSCAR, click here.
Accelerated Risk Management (ARM)
The Law of Constraints was made to be broken! Better, faster, and cheaper is actually an option. ARM is an expert system that makes it faster and cheaper to perform better risk assessments—to ensure every critical risk to your data has been analyzed.
ARM lets you analyze risk successfully without deep subject matter expertise, and takes subjectivity out of the equation. By automatically documenting every risk analyzed and verifying whether your controls reduce risk to an acceptable level, ARM makes the risk assessment updates that ISO 27001 requires almost effortless, streamlining both internal and external audits.
To find out more about ARM, click here.
Policy Automator
Updating policies is probably not your day job, or your favorite activity. But you need a comprehensive, up-to-date set of Policies, Standards, and Procedures to achieve and maintain ISO 27001 certification.
To make this onerous, seemingly endless (200+ hours) task much less painful and error-prone, we created Policy Automator. It’s a simple, elegant way to automatically generate the comprehensive policy documentation required for ISO 27001. As part of the service, your Pivot Point Security team will refresh your policies annually to reflect external or internal changes.
To learn more about Policy Automator, click here.
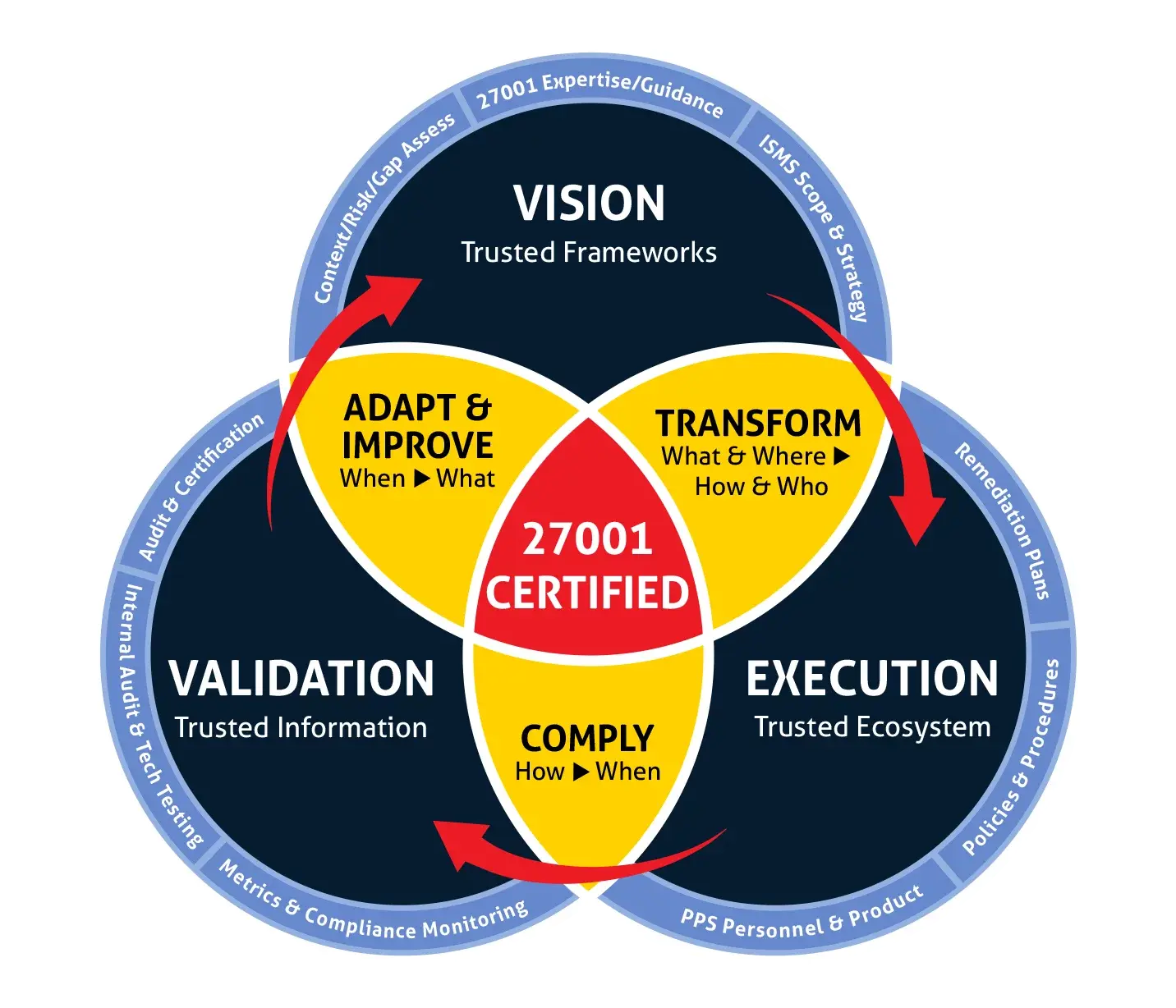
Our Proven Process for ISO 27001
Based on our collective experience across thousands of successful information security engagements over 21+ years, Pivot Point Security has a 3-step Proven Process that we adapt and apply to everything we do.
Our core focus—serving as a trusted partner to help our clients become provably secure and compliant—sits at the center of our process. To achieve that result, four things need to happen:
- You need a Vision of how to move from where you are to where you want to be.
- You need the Trusted Frameworks (e.g., ISO 27001) and Trusted Ecosystem necessary to Execute your vision.
- You need the Trusted Information necessary to Validate that you’re achieving the intended results.
- You need a Proven Process to bring it all together.
Here’s how our Proven Process fits together.
For a quick PDF summary of our proven process, click here.
For an executive briefing video on our proven process, listen to this podcast with Pivot Point Security CISO and Managing Partner, John Verry.
ISO 27001 “Extensions” for Privacy and Cloud
As part of the ISO 27000 family of standards, you can “extend” your ISO 27001 certification in several ways to increase the value of your security program and your “provably secure and compliant” attestations.
ISO 27701 Privacy Information Management System (PIMS)
More and more organizations need to prove to customers, regulators, and other stakeholders that they can secure personal data and comply with legislation like CCPA and GDPR.
For companies that have (or will have) an ISO 27001 certificate, the ideal proof of a robust privacy program is an ISO 27701 certificate. ISO 27701 is a “privacy extension” that turns your Information Security Management System (ISMS) into a privacy information management system (PIMS).
Click here to learn more about our ISO 27701-as-a-service offering.
ISO 27018: Data Privacy for CSPs
Proving you can securely process personal information (PII or PI) in your cloud environment can be a major challenge. Yet new and longstanding privacy regulations (GDPR, CPRA, VCDPA) combined with growing pressure from customers, regulators and other stakeholders make this capability imperative.
ISO 27018 is a code of practice for protection of personal data in public clouds, specifically geared for PII processors. ISO 27018 extends the information security controls in ISO 27002 (the recommended controls for ISO 27001).
CSPs can extend the scope of their ISO 27001 compliant Information Security Management System (ISMS) with additional controls to achieve conformance with ISO 27018. However, unlike ISO 27701, ISO 27018 is not a “certifiable” standard.
Click here to learn more about our ISO 27018 consulting services.
ISO 27017: Cloud Security for CSPs
If you’re a CSP, you’re probably under more pressure to “prove security” than perhaps any other business.
For CSPs that have (or will have) an ISO 27001 certificate, an excellent way to demonstrate strong cloud security is to extend the scope of your ISO 27001 Information Security Management System (ISMS) to include the ISO 27017 controls, leveraging targeted ISO guidance.
Click here to learn more about our ISO 27017 consulting services.