Simplify the Security of Your Connected Devices
As you know, the Internet of Things, or IoT, refers to the billions of physical devices worldwide that are now connected to the internet, collecting and sharing data.
Its promise is limitless; it continues to transform major sectors of our lives including building automation, agriculture, energy, transportation, and medicine. Its peril is nearly as limitless; necessitating new approaches to the secure design, manufacturing, deployment, use, and validation of our respective IoT footprints.
Sun Tzu once said, “If ignorant both of your enemy and yourself, you are certain to be in peril”, well said, and as true today as it was 2,500+ years ago.
With expert guidance and security assessments built specifically to test an ecosystem of connected devices, you can understand the security gaps in your IoT environment and have a clear path to address those gaps.
Your IoT ecosystem may be complex … Let’s keep your security simple.
Although the individual components of securing communications between connected devices and people remain fairly simple, the shear volume of communication and communication channels within IoT creates strategic and logistical challenges:
- How can we accurately map data flows and communication channels?
- What level of security do we need at each end point and for each data type?
- How do we know what security initiatives to prioritize?
- How do we effectively and efficiently comply with laws and regulations like CCPA, GDPR, PCI, SB-327, NISTIR-8228, OWASP IOT, etc.?
- How do we demonstrate to customers their information and privacy are secure with us?
You may have had one “door” to protect per device in the past; now it could be 4, 5, 6, or dozens per endpoint. But don’t let that stop you!
The first step… understand what is driving your need for security
It’s likely one or more of these drivers are the reason(s) you are reading this today. Which ones apply to you?
- Regulation(s) – Many regulations now require organizations to assess the security of their IoT environments. The key here is knowing exactly how much (and how little) assessment you need to ensure you are “compliant”.
- Customer(s) – If your customers (or management or a regulator) need proof your environment is safe, you may have options regarding how you demonstrate that proof. It’s essential to know what form(s) of attestation will work best for you and your customers.
- Partner(s) – Cloud services like Alexa and Spotify are putting up walls and building moats around their cloud environments and requiring proof that you can leverage their services securely (often requiring that you comply with their particular requirements). If accessing third party cloud services to extend your product ecosystem is a must, so then is complying with its security demands.
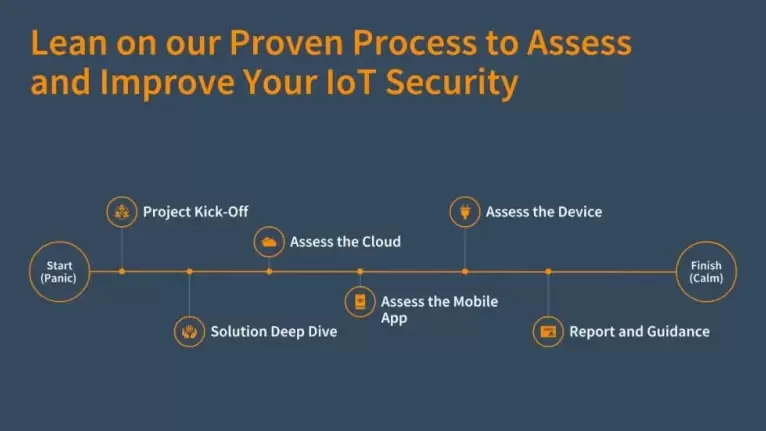
Although every engagement is a little different, Pivot Point Security has developed a proven process for assessing IoT device and platform security and successfully identifying the risk(s) it poses and how to mitigate them.
Here is a quick overview of the steps involved:
Project Kickoff
Getting out of the gate right is critical to your project’s success. At the Project Kickoff Meeting you meet the assessment team (if you have not already), reconfirm objectives, iron out logistics, initiate data requests, and schedule your work effort.
Solution Deep Dive
IoT testing requires that we have a thorough understanding of your end to end solution, not just the devices. We do this via; interviews with your product specialists, demonstrations of key solution components, artifact review (e.g., manuals, specifications, data flow diagrams), initial device installation/use, and any additional required research (e.g., communication protocols, published vulnerabilities).
Whether its 900 Mhz Spread Spectrum frequency hopping radios, Alexa enabled consumer devices, or Intelligent Vehicles; coming out of the Deep Dive we will work with you to construct a complete testing environment aligned with your test objectives.
Assess the Cloud
Ensuring that your systems, applications, and API’s that are critical to your solutionn (potentially including partners) is figuratively and literally central to ensuring the overall security of your solution. Some combination of Network Vulnerability Assessment/Penetration Test, OWASP ASVS aligned Web App & API Assessment will be performed. The latter will often include; architectural assessment, penetration testing, and code review.
Assess the Mobile App
Most IoT systems include a mobile app (or thick client) that is used to configure and/or operate the device element of the solution. Ensuring the application and the API’s the mobile app leverages are secure is critical to the overall security of your solution. Most frequently we leverage an OWASP Mobile ASVS assessment which includes penetration testing and code review to verify your mobile application achieves target security objectives.
Assess the Device
Device testing generally requires full logical and physical testing (e.g., physical interfaces, network services, control interfaces, communication channels, device hardware, device software):
- Are all physical ports (e.g., debug, serial, USB) properly secured? Can the device be deconstructed to expose other modes of access?
- Are all wired and wireless modes of communication (e.g., Ethernet, WiFi, ZigBee, Bluetooth, 6Low) properly secured?
- Are all supporting systems (e.g., IoT platform, Certificate Authorities, Authentication, configuration/management/monitoring, API’s) and associated communications properly secured?
- Does the device conform with security/privacy requirements (e.g., California SB-327, CIS CSC, TISAX, NISTIR 8228, CCPA)?
- etc.
Report & Guidance
Our work isn’t done until you have a clear and actionable plan to get you where you need to go. To that end:
- We provide you an Executive Summary of our testing and findings to ensure that our work is understood by the “C-Suite”.
- We provide you a Technical Summary of our testing and findings to ensure our work is understood by your folks in IT, IS, and your developers.
- We provide you a Gap Remediation Plan because findings without actionable guidance are as useless as ejections seats on a helicopter.
- We jointly attend a project readout call to walk though our work product and answer any of your questions.
- You get unlimited ongoing support as your team works through your remediation plan.
- You can request re-testing (optional) to confirm the efficacy of your remediation(s).
What you can expect from an IoT Security Assessment from Pivot Point Security
We tailor our testing to your specific objectives, but there is one thing that you can always expect; clear, actionable guidance.
The Result?
Peace of mind. You can rest easy knowing your organization is secure and you can prove it. Life is too short to spend it worrying about things you can straightforwardly address. Our customers are confident in the security of their IoT devices and environment.