NIST Cybersecurity Framework (NCSF)
CBIZ Pivot Point Security has helped hundreds of organizations of all sizes understand their cybersecurity posture utilizing the NIST Cybersecurity Framework (CSF). We use maturity modeling, gap analysis, NIST CSF risk assessments, and more to help organizations understand their current and target cybersecurity posture.
The National Institute of Standards and Technology (NIST) CSF refers to a set of best practices and guidelines designed to aid organizations in reducing and managing cybersecurity risks. The NIST CSF is designed to be flexible and adaptable, allowing organizations across all sectors to apply the framework to their specific needs and circumstances. It promotes a continuous improvement approach to managing cybersecurity risks and encourages collaboration between public and private sectors. It also aims to enhance the security and resilience of the nation’s critical infrastructure.
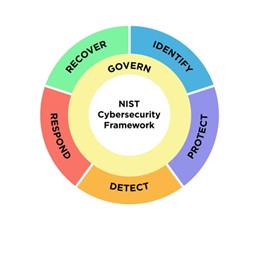
Framework Core Functions
The Framework Core comprises six core functions:
- Govern: Establishing, communicating, and monitoring the cybersecurity policy, expectations, and risk management strategy of the organization.
- Identify: Understanding the organization’s cybersecurity risks.
- Protect: Using safeguards to manage the identified cybersecurity risks.
- Detect: Finding and analyzing potential cybersecurity attacks and compromises.
- Respond: Taking action to deal with a detected cybersecurity incident.
- Recover: Restoring operations and assets affected by a cybersecurity incident.
Implementation Tiers
The NIST CSF Implementation Tiers provide context on how an organization views cybersecurity risk and the processes in place to manage that risk. They help organizations understand their cybersecurity maturity and guide them in enhancing their cybersecurity practices. There are four Implementation Tiers in the NIST CSF, ranging from Tier 1 (Partial) to Tier 4 (Adaptive).
- Tier 1: Partial
- Characteristics: The organization has a limited understanding of cybersecurity risk. Practices are often reactive and ad hoc. There is minimal awareness of risks, and cybersecurity efforts are typically uncoordinated and unplanned.
- Key Aspects: Risk management is sporadic, and there is little or no formal documentation or processes in place. Responses to incidents are typically reactive rather than proactive.
- Tier 2: Risk Informed
- Characteristics: The organization has some awareness of cybersecurity risks and has begun to implement basic risk management tactics. These practices are more structured and repeatable than in Tier 1, but they may still be reactive.
- Key Aspects: Risk management is informed by some policy and procedure, and there is a basic understanding of risk tolerance. There is a stronger focus on identifying and managing risks but with limited integration into the overall business strategy.
- Tier 3: Repeatable
- Characteristics: The organization has established risk management processes that are consistently implemented and tracked. There is a proactive approach to cybersecurity, with practices becoming more formalized and integrated into the organization’s operations.
- Key Aspects: Practices surrounding risk management are repeatable and documented, with regular assessments and reviews. The organization has a well-defined strategy for managing risks, and there is a focus on continuous improvement and resilience.
- Tier 4: Adaptive
- Characteristics: The organization’s approach to managing cybersecurity risks is sophisticated, integrated, and adaptive. Its practices are dynamic and resilient, allowing the organization to anticipate and respond effectively to emerging threats.
- Key Aspects: Risk management is advanced, with a high degree of integration across the organization. The organization uses threat intelligence and data-driven insights to anticipate and mitigate risks. Cybersecurity is fully embedded into the organization’s culture and decision-making processes.
Each tier represents a progression in the organization’s maturity and capability to manage cybersecurity risks effectively. By understanding and working toward higher tiers, organizations can enhance their cybersecurity posture and resilience against threats.
The NIST CSF 2.0 Framework Profile is a tool that helps organizations align their cybersecurity activities with their business requirements, risk tolerance, and resources. The profile serves as a customized roadmap to manage cybersecurity risks, enabling organizations to identify and prioritize improvements in their cybersecurity posture.
Key Components of the NIST CSF 2.0 Framework Profile:
- Current Profile: This represents the organization’s existing cybersecurity practices and the current state of its cybersecurity posture. It includes the outcomes and activities that the organization is presently undertaking to manage cybersecurity risks.
- Target Profile: This defines the desired state of the organization’s cybersecurity posture. It outlines the outcomes and activities the organization aims to achieve in order to effectively manage cybersecurity risks in alignment with its business objectives and risk management strategy.
- Gap Analysis: By comparing the Current Profile with the Target Profile, CBIZ Pivot Point Security helps organizations identify gaps in their cybersecurity practices. This analysis highlights areas where improvements are needed to reach the desired level of cybersecurity maturity.
- Action Plan: Based on the gap analysis, organizations can develop a prioritized action plan to address identified gaps. The plan includes specific steps, timelines, and resources required to implement improvements and achieve the Target Profile.
How We Develop a NIST CSF 2.0 Framework Profile:
At CBIZ Pivot Point Security, we develop a NIST CSF 2.0 framework profile by following these approach:
- NIST CSF assessment: CBIZ Pivot Point Security conducts a thorough assessment of the organization’s current cybersecurity practices, using the NIST CSF’s Core Functions (Govern, Identify, Protect, Detect, Respond, Recover) as a guide.
- Define Goals: We help you establish clear, measurable cybersecurity goals aligning with the organization’s business objectives and risk tolerance.
- Create Profiles: We develop your Current Profile by documenting existing practices and the Target Profile by defining desired outcomes and activities.
- Analyze Gaps: We perform a gap analysis to identify discrepancies in the current and Target Profiles.
- Develop Action Plan: We create a detailed action plan to address the gaps, including plans of action and milestones (POAMS).
- Implement and Monitor: We work with you to execute the action plan, monitor progress, and adjust as necessary to ensure continuous improvement and alignment with the Target Profile.
CBIZ Pivot Point Security uses these methodologies to help organizations effectively measure their current cybersecurity posture and better manage cybersecurity risks.
Benefits of Implementing the NIST CSF
Your organization can experience these advantages once you implement NIST CSF:
- Enhanced risk management provides a structured approach to identify, assess, and manage cybersecurity risks.
- Improved communication establishes a common language for discussing cybersecurity risks and strategies, which helps in communication between technical and non-technical stakeholders.
- Regulatory alignment assists in meeting regulatory and compliance requirements by aligning with recognized standards.
- Continuous improvement promotes regular reviews and assessments, helping organizations continuously improve their cybersecurity measures.
Why Trust Us for NIST CSF Guidance?
CBIZ Pivot Point Security has developed deep expertise in the NCSF by helping hundreds of clients leverage the NIST Cybersecurity Framework to assess and improve their cybersecurity programs. Our extensive experience working with diverse organizations gives us a unique perspective on aligning with trusted and widely recognized security standards. This advantage ensures our guidance is effective, consistent, independent, and actionable. We are your dedicated source for information assurance, focusing solely on information security to provide specialized expertise.
We become an extension of your team, helping you navigate the complexities of the NIST CSF and providing support precisely when you need it. New to security frameworks and assessments? We can help. Our team will ask the right questions, efficiently determine the appropriate scope of your CSF implementation, accurately assess your current maturity level, and ultimately accelerate your journey to a better security posture.
NIST Cybersecurity Framework FAQs
The NIST CSF is a set of voluntary guidelines developed by the National Institute of Standards and Technology to help organizations manage cybersecurity risks. It provides a systematic methodology and common language for risk management in cybersecurity.
The NIST CSF is designed to be flexible and applicable to organizations of all sizes, sectors, and maturities. While it was initially developed for critical infrastructure, it has been widely adopted across various industries to enhance cybersecurity practices.
Implementing the NIST CSF helps organizations:
- Improve their cybersecurity posture by providing a structured approach to managing cybersecurity risks.
- Facilitate communication of cybersecurity practices among internal and external stakeholders.
Take Steps to Strengthen Your Cybersecurity Posture Today
Navigating the complexities of cybersecurity doesn’t have to be a hassle. With tailored guidance from CBIZ Pivot Point Security, you can empower your organization to become more secure with the NIST CSF framework. Let our expertise and experience be your advantage in strengthening your defenses and achieving your security goals. Contact us today to get started.






