Last Updated on February 18, 2025
As mobile devices and mobile apps have proliferated in every business and personal/consumer scenario, so has the need for mobile app security. Data accessible on mobile apps now includes not just personal or credit card/financial data but, increasingly, highly sensitive corporate data from business “systems of record,” which is being exposed to mobile developers via APIs.
Mobile app security guidelines are not well understood by most mobile developers. Penetration testing of mobile applications is challenging and guidelines are still evolving. Hackers, on the other hand, are having no problem finding and exploiting mobile vulnerabilities. Most organizations are now rightly concerned about mobile security, and increasing regulatory scrutiny and data integrity requirements are driving businesses to secure access to mobile data.
While the basic idea behind mobile penetration testing is familiar (“think like a hacker”), mobile penetrating tests are unlike traditional penetration tests in many ways. Mobile devices are embedded devices, so they run on a non-extensible hardware platform with a CPU that’s far different from familiar Intel platforms. And while mobile systems offer growing levels of RAM and persistent storage, they overall lack the capabilities of traditional computing environments.
Despite the disparities between mobile and traditional platforms, we can apply familiar competencies from web app security like threat modelling, risk analysis, bug tracking and report preparation to the analysis and remediation of mobile device vulnerabilities. But the implementation and delivery of attacks to mobile devices can be very different—encompassing apps, Wi-Fi, Bluetooth, flash memory and more, as shown in Figure 1.
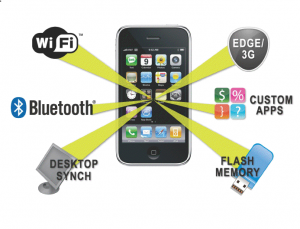
Figure 1: Mobile device attack vectors
Mobile form factors themselves also create unique security concerns. These include:
- Physical security. Mobile phones frequently are lost or stolen. Whether it’s a personal device or company-owned, it’s far more likely than even a laptop to end up in unauthorized hands, thus putting all the data accessible via apps on the device at risk.
- Weaker authentication. Strong passwords (longer combinations of letters, numbers and special characters) are more difficult to type on mobile devices. Thus enforcing strong authentication or multi-factor authentication is often more difficult on mobile devices.
- Direct access to data. Traditional client operating systems support multiple users, each with a different environment. On mobile devices, there are as yet no multi-user environments. Anyone entering the correct PIN will have access to the same apps and data.
- Less safe browsing. Smaller mobile form factors mean that some of the information normally displayed in a browser isn’t readily visible to mobile users; e.g., complete URLs. This basically makes a phisher’s life easier by making it harder to see that a site is bogus.
- Malware. As with any device that connects to the web, mobile devices are under threat from viruses, worms, Trojans, spyware and other malware. New computing environments mean new attack classes. Worms that spread through SMS messages or Bluetooth connections are well-known examples.
With mobile apps, pen testing must encompass the complete mobile app environment, from the local app on a user’s device to back-end web services, APIs and data stores. Application “sandboxing” is commonly used for mobile app pen testing, but is rarely used in traditional pen testing.
In Part 2 of this post I’ll discuss mobile app pen testing tools and techniques.
To discuss penetrating testing services for your business-critical mobile applications, contact Pivot Point Security.


























