Last Updated on January 29, 2025
As someone whose SIEM experience started nearly 17 years ago with eSecurity, Network Intelligence and Protego Networks, I find the recent resurgence in the SIEM space very interesting. The list of drivers is long and includes the latest high-profile breach, significant venture/private equity money in the game, the promise of AI, and regulatory requirements around logging and incident response capabilities.
Over that 17-year stretch, we have had the (mis)fortune of deploying various SIEM solutions in some of the world’s largest organizations, as well as deploying OSSIM and Grey Log solutions into many small to medium sized businesses. We even coded a custom SIEM for one of the world’s largest telecommunications firms, which scaled to 1 billion events per day in 2005, and then migrated that software into the Security Operations Centers (SOCs) of two MSPs and operated it on their behalf for several years.
The anomaly engine we developed (think pre-AI AI) turned into OSCAR—something we referred to as a “headless SOC.” It was an incredibly clever idea, and an awesome answer to a question no one was asking.
Humbled, SIEM took a bit of a back seat as our ISO 27001 and SOC 2 services took off. But now, as our vCISO services are also taking off, we are once again regularly engaging in the “which SIEM?” discussion.
The good news is that there are a lot of great SIEM products and services on the market: Old standbys like LogRythm, QRadar, AlienVault and Splunk; promising newcomers like Darktrace, Exabeam and Elastisearch; and established complimentary products that are incorporating SIEM capabilities, like SolarWinds and Manage Engine.
The bad news is that there are a lot of great products and services on the market, which means that making a decision is easy… but making a great decision is very hard. The situation is exacerbated by the fact that making a bad decision, even on a great product, can result in abject project failure.
Unfortunately, finding the SIEM tool that is “just right” for your organization can require a sizable investment of time and expertise. I think the first best step is to explicitly define your most critical requirements.
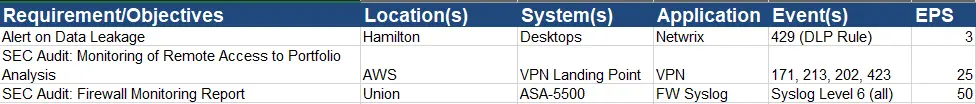
A “cheat” is to think about the report that you will need to get from the SIEM tool, and then work backwards to understand the systems, applications, and specific event logs that will be needed to create that report. Your list might look something like this:
You can then use that information to contextualize a review of the following attributes of the solutions that you are considering:
- Administration
- Ease of deployment
- Cloud environments
- Information capture
- Log and data management
- SEM: Real-Time Event Management and Correlation
- Incident response and management
- Reporting capabilities
- Advanced analytics
- Business context and security intelligence
- Advanced threat defense
- Managed or co-managed options
- Virtualization support
- Operating system support
- Network and security devices/applications
- Data access monitoring
- Identity and access monitoring/integration
- Application integration
Done right, you should land in a successful place. It worked for us.
FYI, we shortlisted three tools that we were confident could meet our near- and long-term objectives:
- We really appreciated the scalability and robustness of Splunk. But the need to learn its query language plus the fact we would need to add some additional IDS and Asset Management tools to meet our requirements made this SIEM bed “too hard.”
- We were really intrigued by Darktrace’s machine learning feature and its ability to visualize an entire network’s activities. But we struggled with the learning curve and its cost, making this SIEM bed “too soft.”
- AlienVault’s integration of key tools we needed (Asset Management, NIDS, threat feed), ability to deploy it in hours, and its affordable price point, made this SIEM bed “just right.”
If you would like to chat and get a copy of the spreadsheet we used to evaluate options, please contact us via the form on our website and we’ll be happy to share it.