Last Updated on March 27, 2025
The US Department of Defense (DoD)’s current NIST 800-171 self-attestation regime mandates the same “one size fits all” requirements regardless of an organization’s size or role. In contrast, the new Cybersecurity Maturity Model Certification (CMMC) framework defines five levels of compliance requirements to better fit an organization’s actual risk profile.
The more flexible CMMC levels “right-size” a supplier’s compliance requirement based on the data it handles. DoD RFIs and RFPs will specify the CMMC level(s) required for prime contractors and their subcontractors.
The five CMMC levels range from Level 1 (Basic Cyber Hygiene—the minimum requirement for any firm participating in DoD contracts) to Level 5 (Advanced, designed to protect high-value assets from advanced persistent threats (APTs)). NIST 800-171 compliance roughly corresponds to CMMC Level 3, “Good Cyber Hygiene, but with about 20 additional controls.
The CMMC’s primary purpose is to safeguard Controlled Unclassified Information (CUI). DoD contract participants that will handle CUI will need to be certified to CMMC Level 3 or higher. To be certified against any of the five CMMC levels, a company must pass an independent third-party assessment, which will be more rigorous at higher CMMC levels. The levels are “cumulative;” to be certified at a given level a business must also demonstrate that it complies with the requirements of all the lower levels.
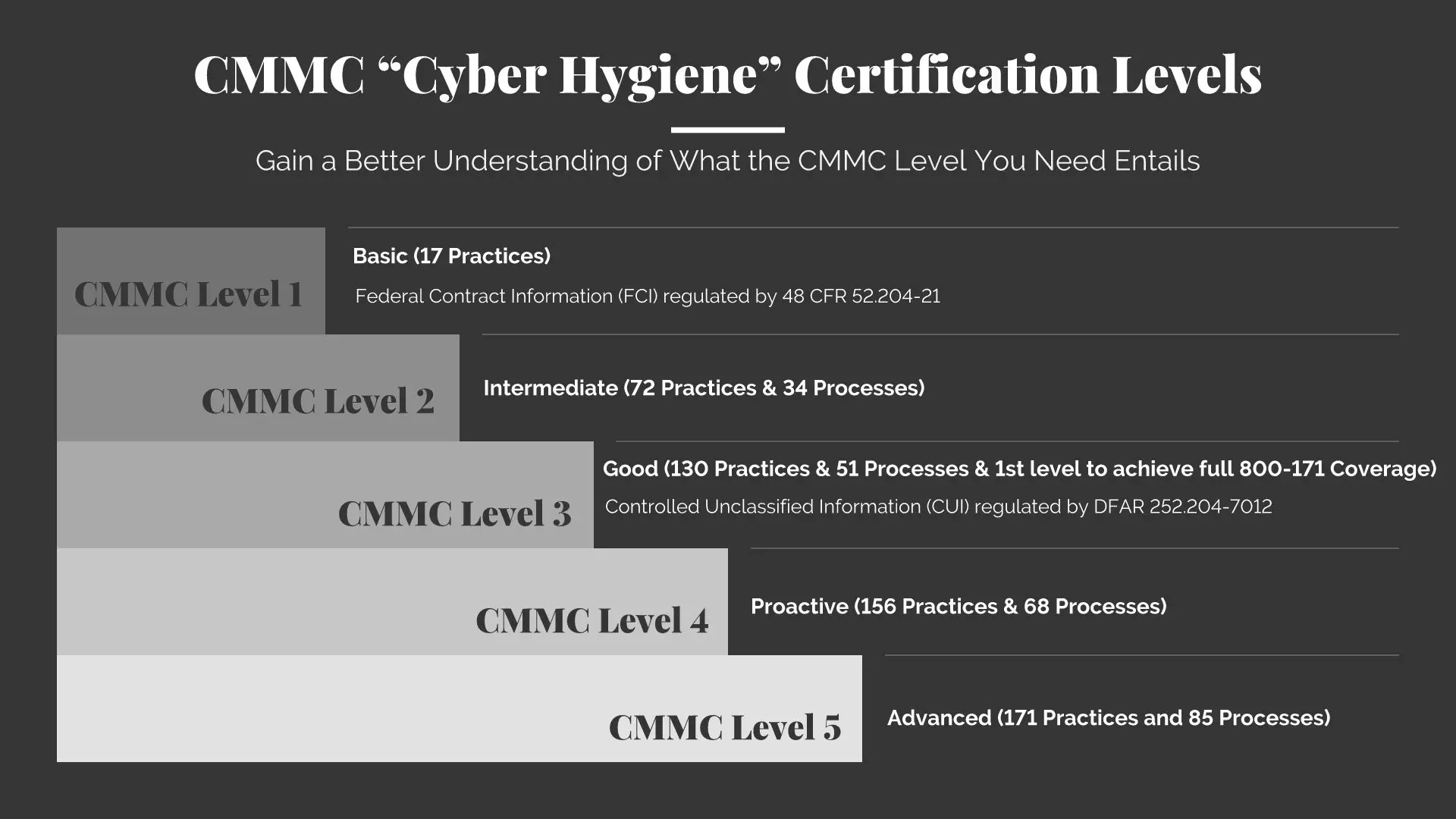
Summary of CMMC Levels
- Level 1: Intended to ensure a company can safeguard Federal Contract Information (FCI)
- Level 2: This is a temporary level meant to serve as a “transaction step” from Level 1 to Level 3
- Level 3: Intended to ensure a company can protect Controlled Unclassified Information (CUI)
- Level 4-5: Intended to ensure a company can protect Controlled Unclassified Information (CUI) even against Advanced Persistent Threats (APTs) and nation state actors. In practice, the DoD expects that most organizations that achieve Level 4 will continue on to Level 5, making Level 4 a “transition step” similar to Level 2.
CMMC Practices and Processes
Each of the five CMMC levels also defines an associated set of practices and processes that apply to all the domains (analogous to “control families” in NIST 800-171) at that level. To pass its assessment and achieve certification at a particular level, a company must demonstrate that it has both operationalized the processes for that level (and preceding levels) and implemented the associated practices. These compliance details help align each level with the type and sensitivity of data to be protected and the anticipated threats targeting organizations holding such data.
Here are the practices and processes associated with each of the CMMC levels as they appear in the current version of the CMMC standard:
CMMC Level 1
Processes: Performed
Level 1 requires that an organization performs the specified practices. Because the organization may only be able to perform these practices in an ad-hoc manner and may or may not rely on documentation, process maturity is not assessed for Level 1.
Practices: Basic Cyber Hygiene
Level 1 focuses on the protection of FCI and consists only of the 17 practices that correspond to the basic safeguarding requirements specified in 48 CFR 52.204-21 (“Basic Safeguarding of Covered Contractor Information Systems”) [3].
CMMC Level 2
Processes: Documented
Level 2 requires that an organization establish and document practices and policies to guide the implementation of their CMMC efforts. The documentation of practices enables individuals to perform them in a repeatable manner. Organizations develop mature capabilities by documenting their processes and then practicing them as documented.
Practices: Intermediate Cyber Hygiene
Level 2 serves as a progression from Level 1 to Level 3 and consists of a subset of the security requirements specified in NIST SP 800-171 [4] as well as practices from other standards and references. Because this level represents a transitional stage, a subset of the 75 required practices reference the protection of CUI.
CMMC Level 3
Processes: Managed
Level 3 requires that an organization establish, maintain, and resource a plan demonstrating the management of activities for practice implementation. The plan may include information on missions, goals, project plans, resourcing, required training, and involvement of relevant stakeholders.
Practices: Good Cyber Hygiene
Level 3 focuses on the protection of CUI and encompasses all of the 110 security (practices) specified in NIST SP 800-171 [4] as well as 20 additional practices from other standards and references to mitigate threats.
CMMC Level 4
Processes: Reviewed
Level 4 requires that an organization review and measure practices for effectiveness. In addition to measuring practices for effectiveness, organizations at this level are able to take corrective action when necessary and inform higher level management of status or issues on a recurring basis.
Practices: Proactive
Level 4 focuses on the protection of CUI from APTs and encompasses a subset of the enhanced security requirements from Draft NIST SP 800-171B [6] as well as other cybersecurity best practices. These additional 26 practices enhance the detection and response capabilities of an organization to address and adapt to the changing tactics, techniques, and procedures (TTPs) used by APTs.
CMMC Level 5
Processes: Optimizing
Level 5 requires an organization to standardize and optimize process implementation across the organization.
Practices: Advanced/Proactive
Level 5 focuses on the protection of CUI from APTs. The additional 15 practices increase the depth and sophistication of cybersecurity capabilities.
Next steps
What CMMC level should your business aim for? That depends on your role in DoD contracts, as well as your current NIST 800-171 compliance level. In particular, suppliers that are subject to a current DoD contract with a Section 7012 (DFARS 252.204-7012) clause will need to pass a CMMC Level 3 assessment when the contract is renewed.
Pivot Point Security offers a full spectrum of CMMC advisory and consulting services, including how to leverage ISO 27001, SOC 2 and other security attestations to prepare for CMMC. Contact us today to connect with a CMMC expert about your company’s unique compliance scenario.