Last Updated on January 18, 2024
I previously blogged about NIST 8259 and NIST 8228, and how they can help your business understand, design and test the security of Internet of Things (IoT) devices.
While NIST 8259 and NIST 8228 are both useful documents, they have limitations:
- Neither provides sufficient guidance for a product/design team to develop a secure end-to-end IoT solution.
- Neither gives a security testing team sufficient guidance to assess the security of an IoT solution.
Why? Both 8259 and 8228 are very IoT device centric, which is just one (very important) component of a complete IoT solution.
The bulk of the IoT solutions that we test include:
- A web-based portal application for managing the devices/solution
- A number of servers (e.g., web server, app server, authentication server, database server, bastion server, etc.) hosted in one or more data centers
- APIs consumed by the web app, partners/clients, mobile apps, and thick clients
- iOS and Android mobile apps used for configuring/managing/using the device and/or interacting with the portal app
- One or more connected devices that talk to each other, the mobile app, cloud APIs, and perhaps third-party clouds (e.g., Cradlepoint, Alexa, Spotify)
Thus, it’s clear that IoT design and testing efforts would both benefit from some additional, non device specific guidance. This is where the Open Web Application Security Project’s Application Security Verification Standard (OWASP ASVS) and OWASP Mobile Application Security Verification Standard (MASVS) come in.
- OWASP ASVS is the industry’s leading guidance on creating secure applications. In short, it provides explicit guidance on up to 292 control practices across 14 application security domains (e.g., Authentication, Session Management, Access Control, Communications, Error Handling & Logging) that should be in place to ensure that an application is secured consistent with its risk. The number of controls vary based on the risk level of the application. The icing on the cake is that the ASVS includes an appendix that provides additional contextual guidance specific to IoT.
- OWASP MASVS is the industry’s leading guidance on creating secure mobile applications. In short, it provides explicit guidance on 84 control practices across 8 mobile application security domains (e.g., Authentication & Session Management, Cryptography, Resilience) that should be in place to ensure that a mobile application is reasonably secured.
So, does that make ASVS and/or MASVS a better standard than NIST 8259 to support IoT solution design and testing? In my (not so humble) opinion, yes. ASVS and MASVS provide significantly greater coverage of the end-to-end solution than NIST 8259 does. That being said, NIST 8259 does provide specific device guidance of value.
On a recent episode of The Virtual CISO Podcast, Daniel Cuthbert, the OWASP ASVS project lead, said it best: “The ASVS gets rid of that ambiguity because what we found was not many people knew how to properly test applications, and both from a testing perspective and those who are getting tested, there was a lot of, “Have they looked at this? Do we know they’ve looked at this? Do they know they should look at it?” And so on, and that’s where the ASVS comes into play. It’s a standard for testing applications, but more importantly, it allows everybody in the circle to align their requirements and offerings.”
If you are on the IoT design/development side of the equation, I would get your team a copy of the ASVS so that they can “move security (as far) left” in the process as they can.
If you are on the testing side of the equation, I would suggest that testing an IoT solution without using ASVS is like having chips without the guacamole… a lot of noise and no substance.
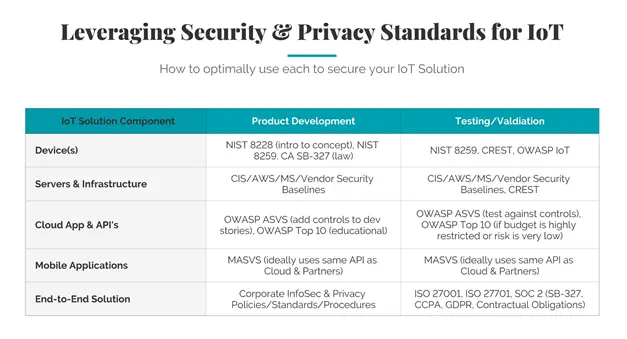
The following table summarizes my ideas and teases some future blogs to address a few other standards that I think are valuable to developing, testing, and operating a secure IoT solution.

IoT Security Roadmap
Proving Your IoT Is Secure & Compliant is Less Complex than You Think In our IoT Security Roadmap we go into detail on how to execute each step of our process.
Download our IoT Security Roadmap now!