Last Updated on January 30, 2025
In part 1 of this post I applied “the 80/20 rule” to cyber security. The goal is to mitigate about 80% of your InfoSec risk with 20% of the effort, by addressing the biggest risk—social engineering and especially phishing attacks.
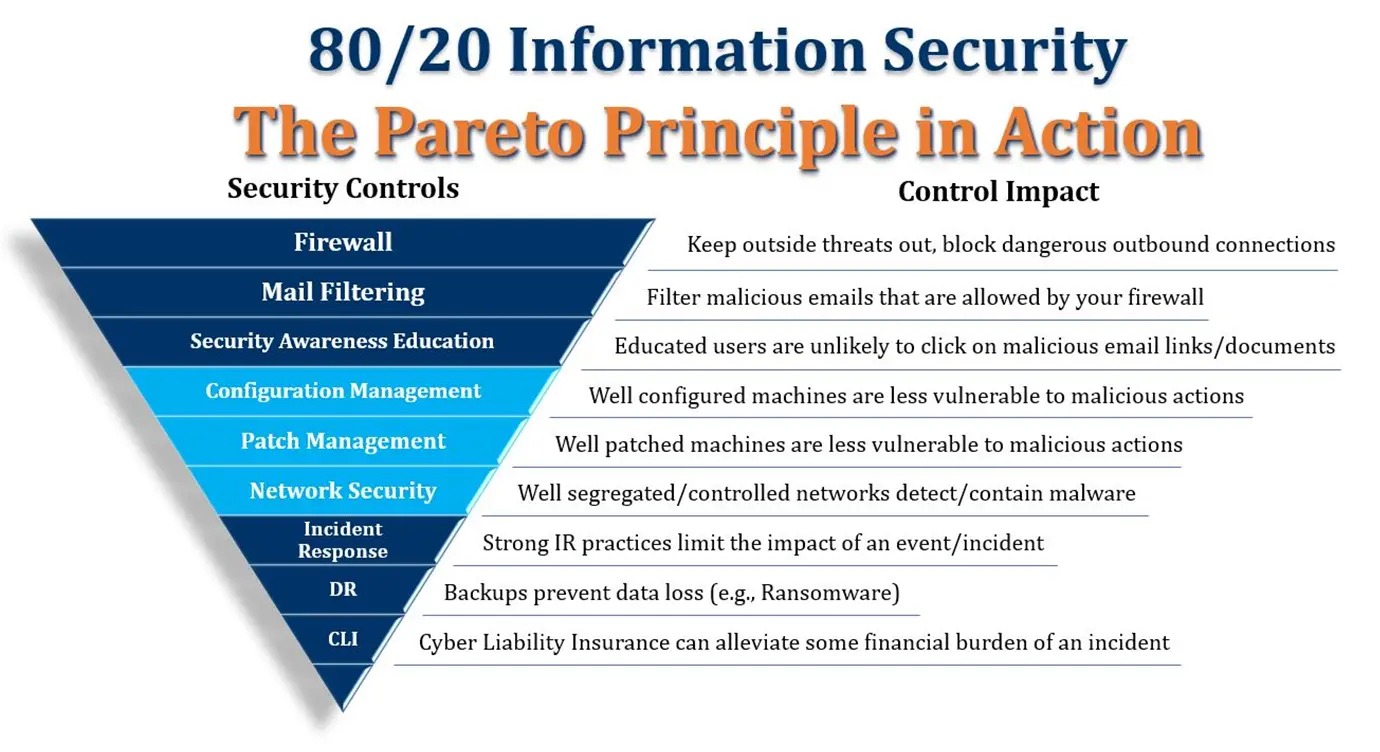
Starting in part 2, I’m explaining the 80/20 cyber security controls “in order,” to show how they mutually support one another.
In this part 3, I’ll cover controls 4, 5 and 6 in the 80/20 approach:
- Configuration management
- Patch management
- Network security
These three controls work synergistically to block ransomware and other malware threats or limit the damage they can do.
Control #4: Configuration management
Because users inevitably make mistakes and click on malicious links or open poisoned documents, you need robust configuration management. That way if malware does escape onto a desktop, it’s configured in such a way (e.g., no local admin user privilege, antivirus and endpoint protection running, logging enabled, etc.) that the desktop isn’t compromised by the attack.
Control #5: Patch management
Patch management is effectively an element of configuration management. While the latter ensures the system’s configuration/settings are correct, the former ensures that all the software on the machine (especially Windows, Office, Adobe products and Google Chrome or other browsers) is up-to-date so that vulnerabilities are minimized.
For example, if a user opens a document in a malicious email that attempts to exploit Adobe Reader’s handling of PDFs, but you have the latest version of the software in which that vulnerability is patched, the poisoned document is unable to cause any real damage.
Control #6: Network security
Patching key applications is one of the very most important cyber security controls you can put in place. But no patching program is perfect, plus you’re still left vulnerable to zero-day threats. This is why you need strong network security.
The idea is to segregate different parts of your network traffic to minimize the potential for attacks to propagate. If you can block malware from spreading from one subnet to another, or from one geographic location to another, that’s a huge win.
With these technical controls in place, you will have greatly reduced your risk of an “incident”—a scenario where malware proliferates across your network and impacts your environment in its entirety. Because the impact can still be large, you should reduce this risk further even though the risk is now much smaller. This is where the last few 80/20 controls come in.
I’ll cover those in the next (and final) post. Thanks once again for your interest. I hope you’re finding these posts valuable for helping you envision how “80/20 cyber security” can help your organization.
Access all posts in this series here: