Last Updated on January 31, 2025
In part 1 of this post I introduced Vilfredo Pareto and “The Pareto Principle” as applied to information security. The goal is to mitigate 80% or more of your InfoSec risk with 20% or less of the effort, by focusing on the most prevalent risk—which is associated with social engineering and especially phishing attacks.
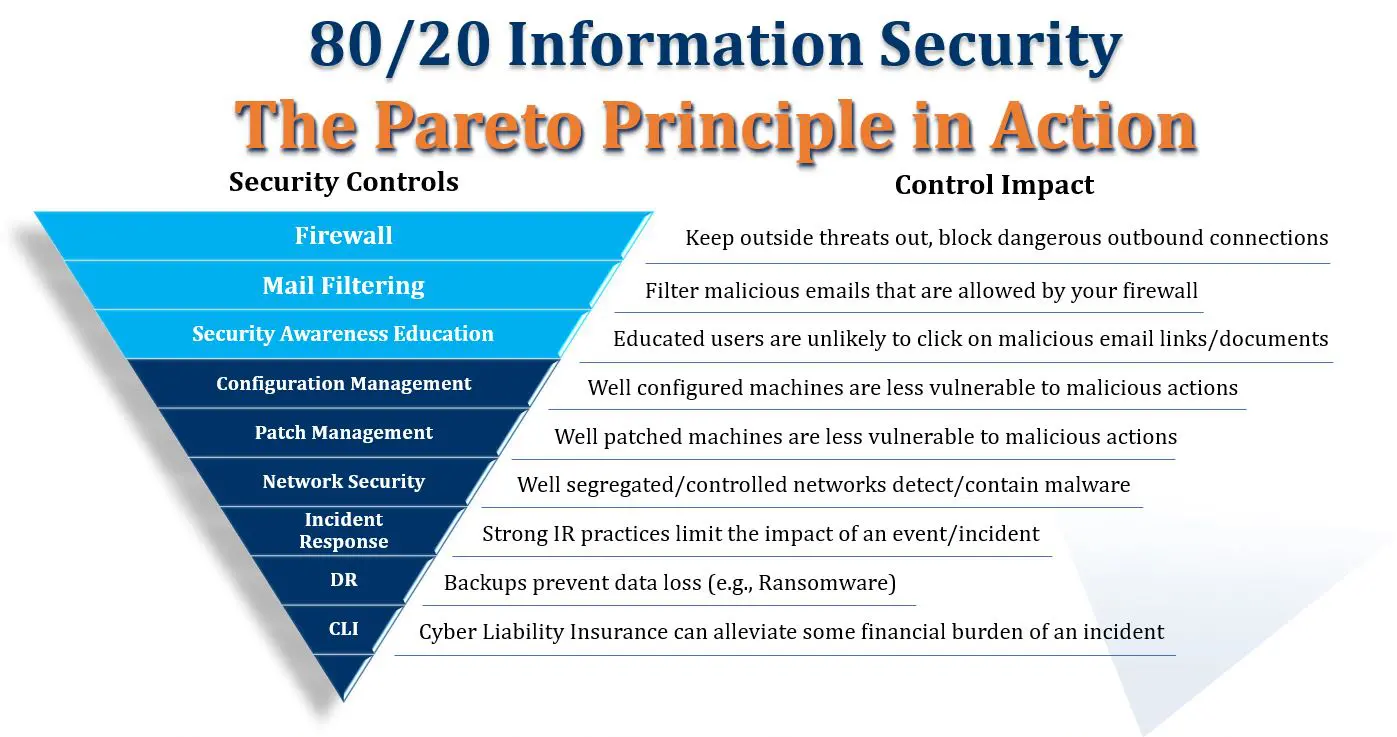
In this part 2, I’ll explain the 3 most critical controls in the 80/20 cyber security controls framework:
- Your firewall
- Mail filtering
- Security awareness education
With these 3 controls solidly in place, you’ll address “80% of the 80%” of your risk associated with social engineering. Note how each control supports the one previously described. If one fails to block an attack, the next one kicks in.
Control #1: Your firewall
A firewall is the “front line” of almost any organization’s information security posture. Basically a firewall acts as a filter. You want to configure it to filter whatever it realistically can so as to minimize your attack surface and reduce the number of threats that make it down to your email server. Implementing geo-gating, web filtering and malicious file blocking on your firewall is a great start.
Control #2: Mail filtering
Of course, in order for email to function and for legitimate messages to not get blocked, some attacks will get past your firewall. This is when mail filtering kicks in. Properly configured to block spam and recognize malicious emails, mail filtering can greatly reduce the number of dangerous attachments and hyperlinks that get through to your users’ inboxes.
Control #3: Security awareness education
No mail filter is perfect, and some malicious messages and poison documents will get past it. At that point, your most critical line of defense is your users. Well-educated users stop more threats than any other control.
If users never made mistakes, the above three controls might successfully mitigate the majority of your organization’s information security risk. But “0% human error” isn’t a realistic goal, and additional 80/20 controls are therefore needed.
I’ll cover those in the next post. Thanks for hanging in there with me, stay safe!
Access all posts in this series here: