Last Updated on January 21, 2025
Every company that handles sensitive data needs a “provably secure and compliant” information security and privacy program that meets organizational objectives and aligns with open, trusted frameworks—thus allowing InfoSec to become a business enabler.
Are you there? Do you have a strategy and a plan to get there?
To help SMBs get a firm grip on security, John Verry, Pivot Point Security CISO and Managing Partner, recorded a special episode of The Virtual CISO Podcast that’s all about “making it easy for the C-Suite to manage cybersecurity.”
John recorded this podcast after a call with a client, who remarked that our “proven process” for helping SMBs become provably secure and compliant is also a great model for helping execs manage their firm’s cybersecurity program. If you think you have a solid security posture, this process will enable you to confirm and demonstrate that. If not, this process will help you get there.
Making cybersecurity a business enabler
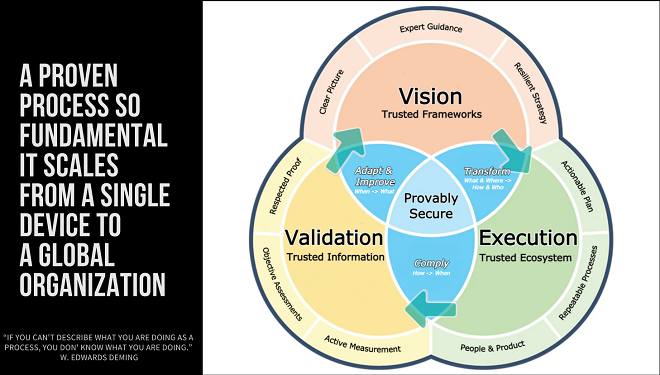
Here are the 3 things SMBs need to achieve provable security and compliance:
- A clear vision of where you are now and where you want to be. In short—a vision for how to make cybersecurity a business enabler.
- Once you have that vision, you need to transform it into an actionable plan that you can execute repeatedly and consistently to drive the outcomes you want.
- Once you’re consistently and repeatedly operating your plan, you need to objectively validate that it’s producing the intended result (i.e., provable security and compliance).
Pretty straightforward… But also pretty simplistic at this 10,000-foot level. How do you get started with actualizing the process? John recommends starting by asking your team three basic questions:
- Do we have an information security and privacy strategy that’s aligned with open and trusted frameworks and our business objectives, which will allow information security to become a business enabler?
- Do we have a set of formally documented, repeatable policies and procedures that has been operationalized as part of our corporate culture and reflects “how we do things”? Put another way, do we have a “trusted ecosystem” of people and tools that operates efficiently and effectively?
- Do we have the evidence we need to validate that our information security and privacy program is functioning as intended? That is, are we complying with what we say we’re doing? Is this activity producing the intended outcome, which is the provably secure and compliant state we need? And does our process generate the “respected proof” we need to demonstrate our security/privacy posture to key stakeholders?
What’s Next?
“If you were to ask just those three questions, and you got answers that made you feel comfortable, you’re probably in pretty good shape,” John remarks. “But I’d say that in very few organizations would you ask those three questions and leave that room sleeping well at night.”
If you hear, “No, no and no,” or get blank looks when you ask those three questions, what’s next? This “drill-down” scenario is where our proven process really shows its worth.
To find out more about applying Pivot Point Security’s proven process at your company, look for more blog posts on this topic. And be sure to listen to this podcast episode with John Verry the way through to learn more about a proven process for achieving and proving compliance: EP#59 – John Verry – Governing Cybersecurity: A Process for Becoming Provably Secure & Compliant – Pivot Point Security
Looking for some more content around establishing and validating a proven security process? Check out this podcast: EP#60 – John Verry – A Guide for Validating Your Security Process – Pivot Point Security