Last Updated on February 13, 2025
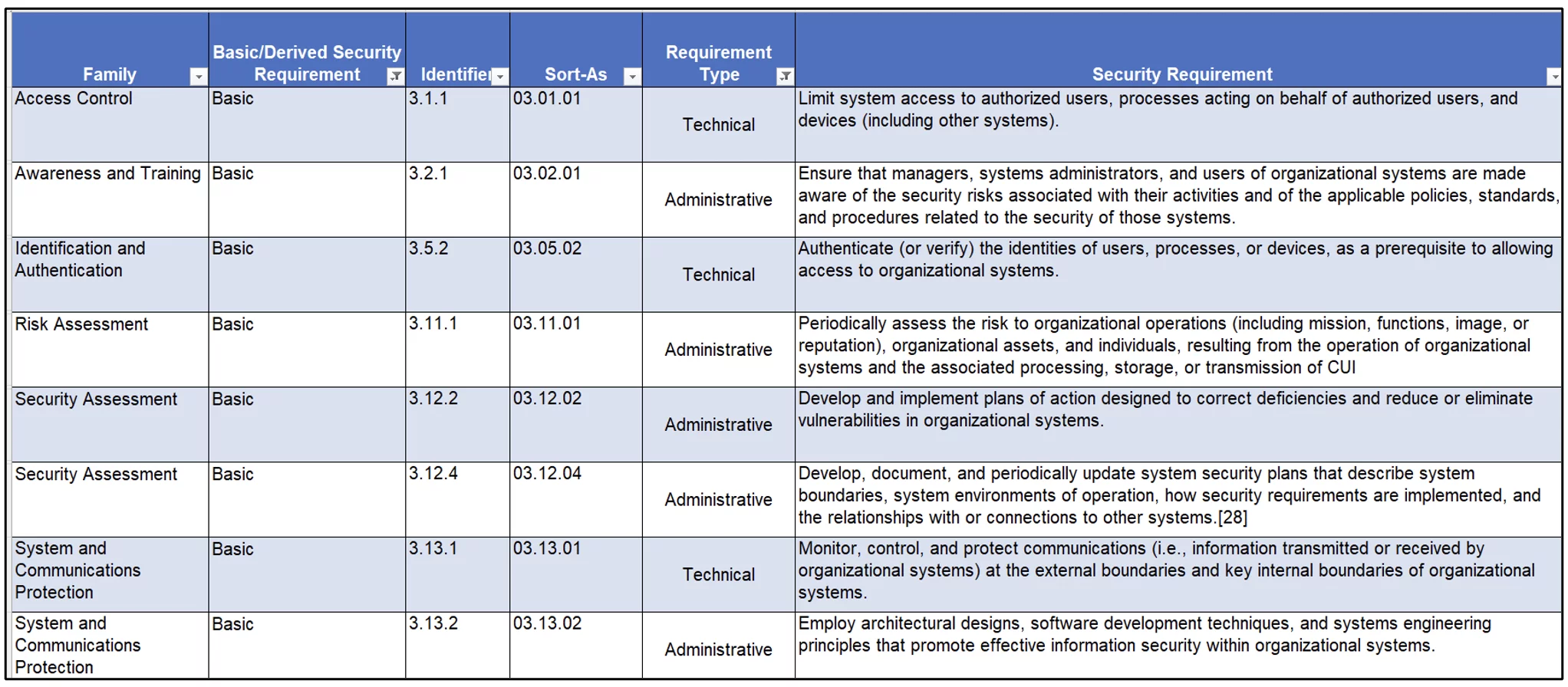
Back in 2016, we created a NIST SP 800-171 requirements matrix (Figure 1) that grouped the security requirements into two categories: Technical and Nontechnical. The goal was to help organizations understand which requirements can be achieved with management and operational controls (e.g., policies, procedures, service level agreements, etc.…), identifying which requirements must be achieved with a technical control, as well as recommending requirements that should be achieved with a technical control, based on feasibility.
Figure 1 – Matrix
Understanding how best to meet the NIST 800-171 security requirements is critical to properly manage risk and implementation cost for your CUI or other information security compliance program.
Divide and conquer
Organizations need to have a clear understanding of their security requirements, which can be used in the system categorization process. Then, the organization can leverage the “categorization” of requirements to break the implementation project into more manageable chunks. While your technical staff work on identifying how to address any technical deficiencies and gaps (this is the “expensive” part), have the “program” team work on your policies, plans, and procedures.
What we mean by this is, organizations shouldn’t have domain architects or systems engineers drafting governance documentation. You should have someone at the program level building the plans to enable your CUI program to “survive the times” by drafting policies that define and communicate what your CUI program intends to achieve (i.e., control the flow of CUI, control, and monitor access to CUI assets, train personnel on how to handle CUI, incident handling and reporting, etc.).
Key plans to create
Your plans are documented steps on how to enforce or sustain the policies. These include your System Security Plan, Incident Response Plan, Disaster Recovery Plan, and your Training Plan, to name a few.
Your processes should be high-level actions designed to enforce a policy or a plan and it should generate a predictive outcome. Your procedures are the more granular actions the operations team, system owner, practice owner, or control owners must take to achieve the approved process (Yes! These generate your organization’s evidence and artifacts).
Prioritizing your security program implementation
For an information security/cybersecurity program, like the CUI program, that includes a predefined set of security requirements like NIST SP 800-171, your organization can take one of several routes:
- Mission Risk: DoD has identified a set of NIST SP 800-171 requirements for which Plans of Action and Milestones (POAMs) are not permitted (those weighed at 3 and 5) for CMMC certification. These should be treated as non-negotiable controls that your organization must achieve. These should be your priority.
- Low-hanging Fruits: These controls will take time to implement, but they require very low financial investments. Get these done as soon as you can. Here we are talking about your CUI Mandatory trainings, which are part of the requirements the DoD has weighted as a ‘5.’ Also in this category are requirements that your organization can achieve with administrative controls.
- For other security requirements, let risk be your driver.
Next steps
For help defining your CUI program, breaking your project into manageable workstreams, or designing a set of plans, contact Pivot Point Security.