Last Updated on January 30, 2025
Over the weekend a friend who was staying with me was targeted in an unusually persistent and sophisticated phishing campaign. Over the course of about three days, she received four emails, each playing off the previous emails in repeated—and enticing—attempts to get her Apple ID credentials.
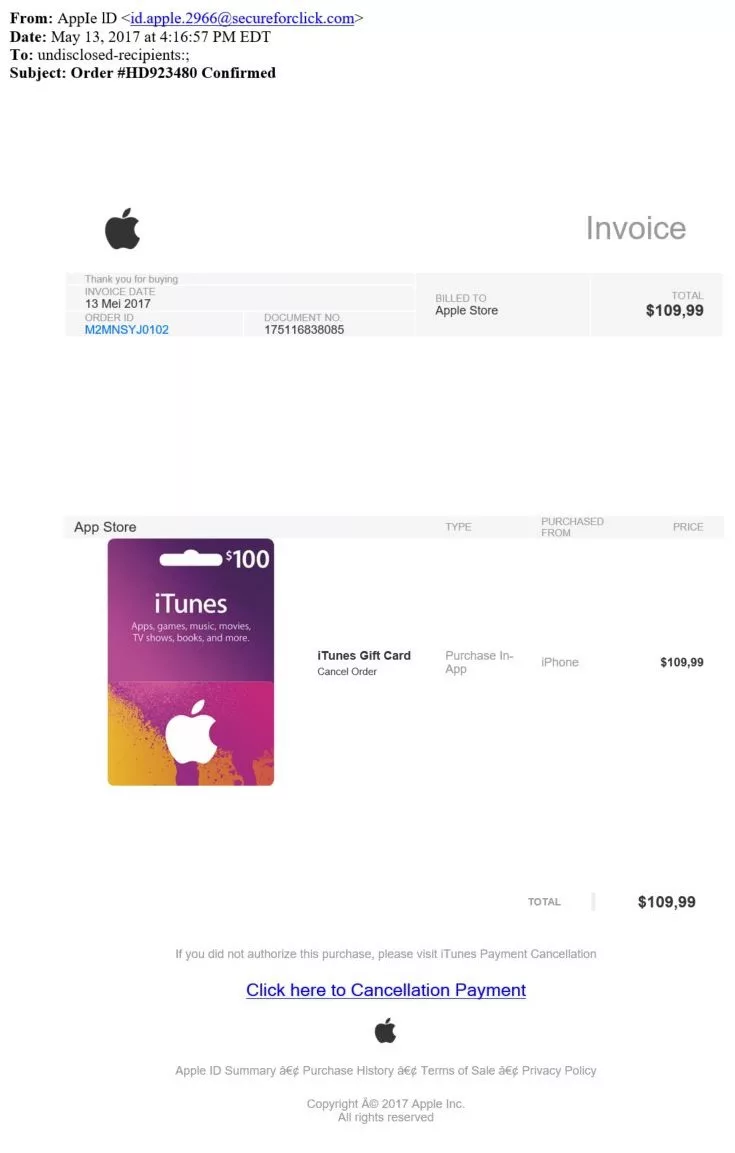
The first email (see the screen shot below) offered her a chance to either confirm or “click to cancel” a bogus purchase of a $100 iTunes card made with her Apple ID. My irate friend said, “Hey, I didn’t purchase anything!” and was about to click through to malware-land when I said “Whoa!” and suggested we take a closer look.
I immediately spotted some clear tell-tale signs this was a phishing attempt, including:
- The email address in the “From:” field was clearly not from Apple
- The “To:” field indicated the email was sent to multiple recipients, though it supposedly related to a single purchase by a single person
- The currency punctuation was non-US (comma, not period), so the email probably originated outside the US, which would be unlikely if it came from Apple
- The text for the link the victim was supposed to click was grammatically incorrect
- Various non-alphabetic characters near the bottom of the message didn’t display correctly, indicating that the email was created using a non-US character set and further confirming it probably originated outside the US
My friend was quickly convinced, while this was a pretty good phish and almost caught her, her Apple account hadn’t really been hacked and she could forget about it.
But about two hours later my friend received a second email from the same sender, also pertaining to her Apple ID. Unfortunately, I don’t have a screen shot of this one, my friend deleted it right away (I can’t blame her). It basically said, “We’ve detected fraudulent activity on your iTunes account. Click to update account information.”
After careful inspection, we both knew this was another Apple ID phishing attempt. Many of the tell-tale signs listed above were in this email as well, but we had to hand it to the clever hackers: Email #2 played on fears of being hacked spawned by email #1. This crafty follow-up no doubt snared some of the recipients who were savvy enough to pass on their first phish.
But the next morning my friend got another email from the hackers regarding her Apple account (which I also failed to capture). This one basically said because Apple had detected fraudulent activity and she hadn’t responded to the previous email as directed, they were going to shut down her account. She was again directed to “click here” and verify with her Apple ID credentials that all was well.
I don’t know how many people fell for this trick but even I, a trained information security expert, would have seriously considered clicking this link. Apple users rely heavily on access to their account and the threat of it being locked out is a big deal.
Fortunately, the hackers again made some traditional mistakes with grammar, punctuation and poor use of the “To:” and “From:” lines. We were able to sniff them out.
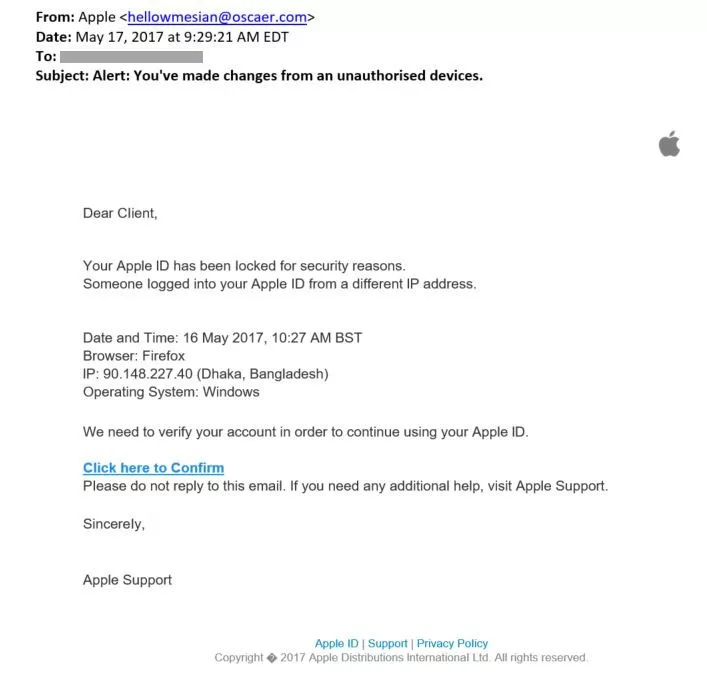
Fast-forward about 48 hours and my friend got a fourth and presumably final email in this sophisticated phishing campaign (see the screen shot below). Again, it played on her concerns about being hacked that the prior emails had inflamed.
This one reiterated her account had been shut down for suspected fraudulent activity and she should click through to reinstate it. This one was somewhat less convincing overall than the prior emails and came from a different email address than the others.
This is the most persistent and convincing email phishing campaign I’ve seen yet. Usually, you get a standalone phishing email and assuming you spot the attack and delete the email that’s the end of it. In this case, the phishers were prepared at each step to entice you with a follow-up that played on the very concerns about fraud the prior emails had spawned. With emails two through four, the victim might well think: “Oh, good, this time they caught it!”
One key takeaway is understanding just how well hackers comprehend human behavior and psychology. I fear this type of emotional manipulation will only cause more people to fall victim to phishing attacks. Realistically these hackers were only a few mistakes away from building the best phishing scam I’ve ever seen.
My friend and I are both waiting to see if she’ll receive any more of these emails. Meanwhile, I suggested she set up two-factor authentication with Apple so that, even if hackers get her username and password, they still won’t be able to hack her account.
Reduce Phishing Risks with Cyber Security Awareness Training
Contact Pivot Point Security to help strengthen your company’s “human firewall” with engaging and effective cyber security awareness training.
For more information:
- Apple’s guidance on how to spot and avoid phishing attempts, and what to do if your Apple ID is compromised
- How to setup two-factor authentication for your Apple devices, so that your account can only be accessed using your trusted devices (e.g., your iPad, not some hacker’s iPad).
- How to report phishing attempts to Apple