Last Updated on November 20, 2025
The virtual chief information security officer (vCISO, aka fractional CISO) role focuses primarily on strategy and governance. But there’s more to the story. A successful vCISO program must be highly adaptable to guide a business through different cybersecurity maturity phases.
This post shares unique insights from experienced vCISO service providers on how changing business needs impact what you should expect from your vCISO engagement.
What are the 3 vCISO service elements?
A maxim worth remembering is, “cybersecurity starts with a plan.” A primary goal of a vCISO engagement should be to help the client develop a risk-aware, business-prioritized strategic plan to enhance their cybersecurity posture.
Organizations need a clear vision that addresses their cybersecurity risks and needs holistically—not just hammering on the scariest current problem. But strategic guidance isn’t the only thing a company needs to build a cybersecurity program.
This is why vCISO services frequently require three elements:
- Advisor—Strategic guidance to support planning, decision-making, and creating a roadmap to move the cybersecurity program forward.
- Implementer—Technical and engineering expertise to turn a roadmap into a working cybersecurity program with actionable policies and processes.
- Operator—Hands-on administrative/operational effort to drive the everyday workings of the cybersecurity program once it has been implemented.
A successful vCISO engagement takes the right balance of advisor, implementer, and operator service elements. Often this means tapping not just an individual vCISO but a wider virtual security team skill set. Even if your vCISO has the know-how to patch your software, for example, this would not be a cost-effective use of their time.
What are “the 3 phases of vCISO”?
A critical factor in understanding what virtual skills mix you need to support your evolving cybersecurity program is the cyber maturity phase your business is moving into or through.
Experience shows that firms seeking vCISO services often find themselves in one of three phases. Each phase tends to have distinct vCISO/virtual security team needs and a distinct vCISO mindset. These phases are:
- Address urgent issues now, then build a cybersecurity roadmap.
- Build a cybersecurity roadmap, then execute/implement it.
- Fully operationalize and optimize the cybersecurity program.
Identifying where you are in this three-phase cyber maturity sequence will help you (and your vCISO provider) dynamically procure the right levels of advisor, implementer, and operator services to efficiently and effectively address both near- and longer-term objectives. The sections that follow share details on each phase.
Phase 1: Address urgent issues
With cybercrime now viewed as the top business risk globally, SMBs increasingly experience a “tipping point” event that escalates cybersecurity (and often privacy along with it) from a nagging agenda item to a business-critical pain point. Typical events that precipitate this shift include:
- A major cyber incident, like a data breach, service disruption, or “failed” regulatory or customer cybersecurity audit.
- Increased market demands or scrutiny by a pivotal client or prospect to prove you can keep sensitive data safe—often by demonstrating compliance with a trusted cybersecurity framework like ISO 27001 or SOC 2.
- A new compliance requirement, e.g., NIST 800-171, GDPR and/or US state-level privacy rules, 23 NYCRR 500, etc.
Orgs in this early phase generally don’t need a lot of vCISO/advisory support upfront, as the circumstances at hand are dictating their short-term “roadmap.” What these firms require is deep “implementer” expertise and bandwidth (in-house and/or third-party) to address their flaming issue, such as achieving ISO 27001 certification, adding controls to reduce specific risks, and so on.
What’s the right amount of vCISO for phase 1? Here the vCISO role is focused on oversight and ongoing direction to ensure that short-term efforts will flow into longer-term objectives.
Phase 2: Build and implement a cybersecurity roadmap
As urgent cyber issues fall under control, the vCISO’s strategic input needs to ramp up to define the company’s longer-term cybersecurity vision. In parallel, implementation efforts ramp down
But phase 2 cyber maturity doesn’t always follow phase 1. Companies can “pass go” and move directly into phase 2 without a precipitating event, usually as the result of a gradual buildup of cybersecurity client demands.
Either way, this phase requires more strategic vCISO input. Central to this process is defining key factors like the scope and context of your cybersecurity program, the data you handle, the vendors you share data with, your customer contractual obligations, regulatory demands, and whatever else impacts your information-related risks and subsequent risk treatment decisions.
An ideal approach to help kick off phase 2 is to adopt a risk model and conduct a risk assessment so you can prioritize roadmap steps based on risk
As the roadmap is gradually executed, companies need more implementation effort relative to vCISO/strategic effort. For example, the vCISO might identify the need for a third-party risk management (TPRM) program, to be executed primarily by a TPRM subject matter expert.
Phase 3: Optimize the cybersecurity program
Once the cybersecurity program is mostly built out, the vCISO’s role shifts again. Vision and strategy remain key, but now the vCISO begins focusing more on program governance and optimization. This phase also requires specific operational skills within the virtual security team
During this open-ended “operate and optimize” stage, vCISO clients often benefit from additional support to keep their program rolling forward. This is especially important if a company needs to maintain compliance with ISO 27001, the NIST Cybersecurity Framework (CSF), or other cyber standard with continuous improvement requirements
In this context, the vCISO typically plays a greater role in charting ongoing direction; and in interacting with management, regulators, customers, and IT/security team members. Phase 3 also requires governance and continuing validation that security controls are operating, security metrics are positive, and contractual, regulatory, and/or certification requirements are met. Implementer services may be required on an on-demand basis to address changes to the program.
What’s next?
For more guidance on this topic, listen to Episode 147 of The Virtual CISO Podcast with guest Matt Webster, Partner at Harbor Technology Group.
Access Your vCISO Implementation Roadmap Now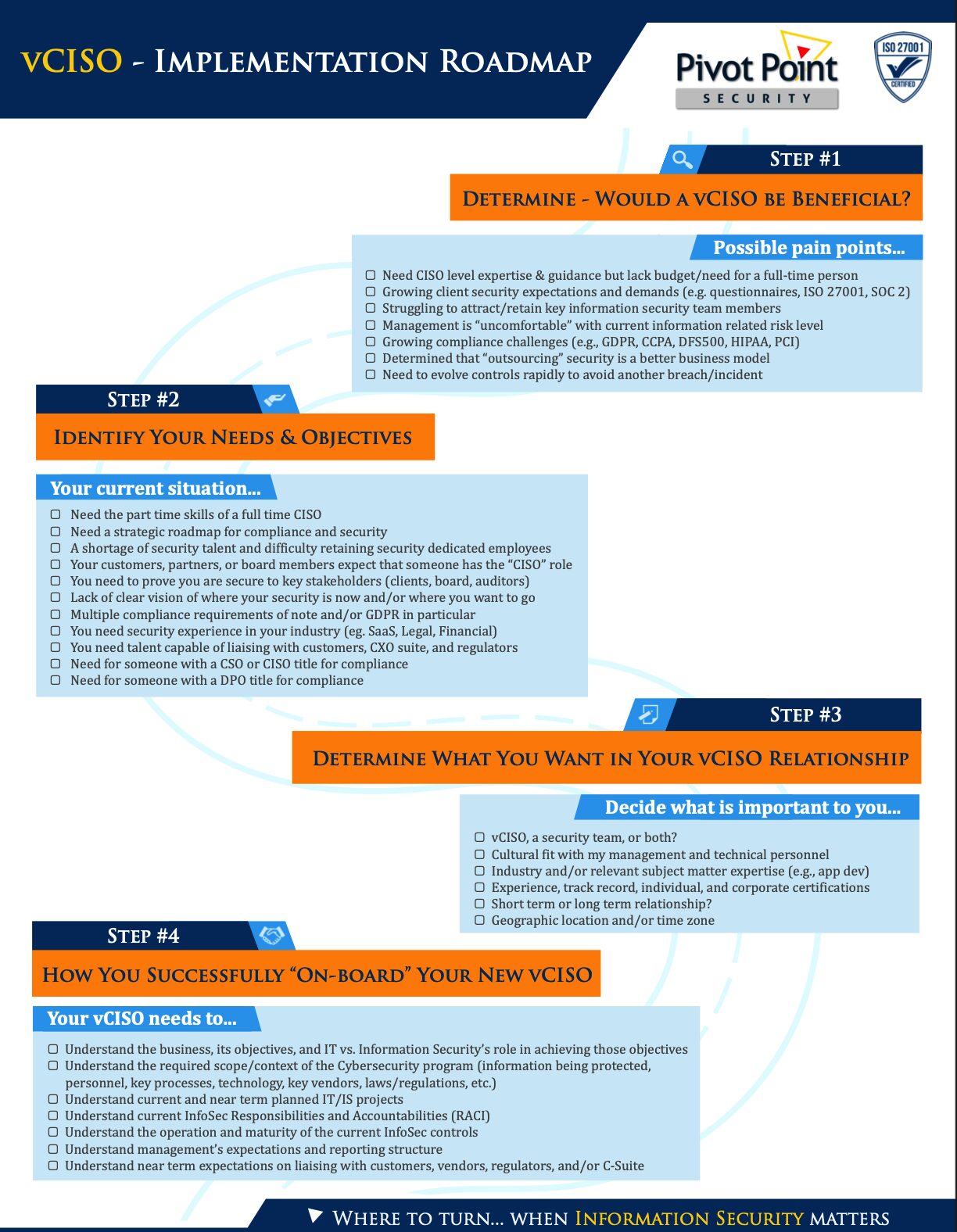



|




























